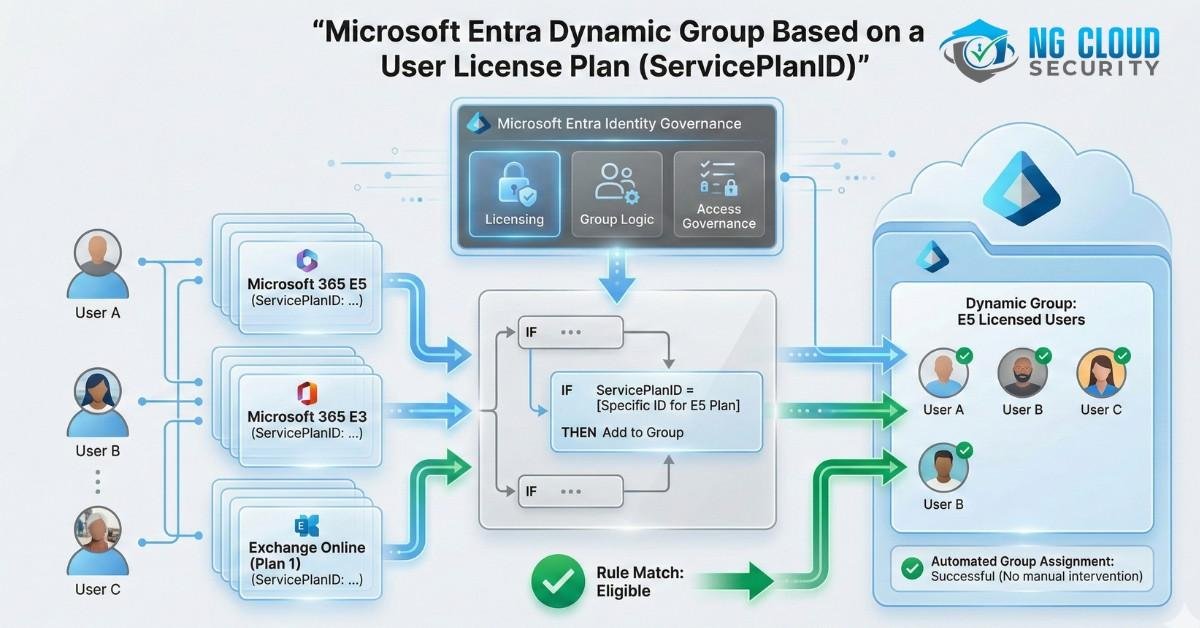
Microsoft Entra offers an excellent feature that allows users to create a Microsoft 365 group based on a set of rules. These rules can dynamically query user attributes to identify specific matching conditions. For instance, one can create a dynamic membership rule that adds users to a particular group based on their “state” property. For example, […]
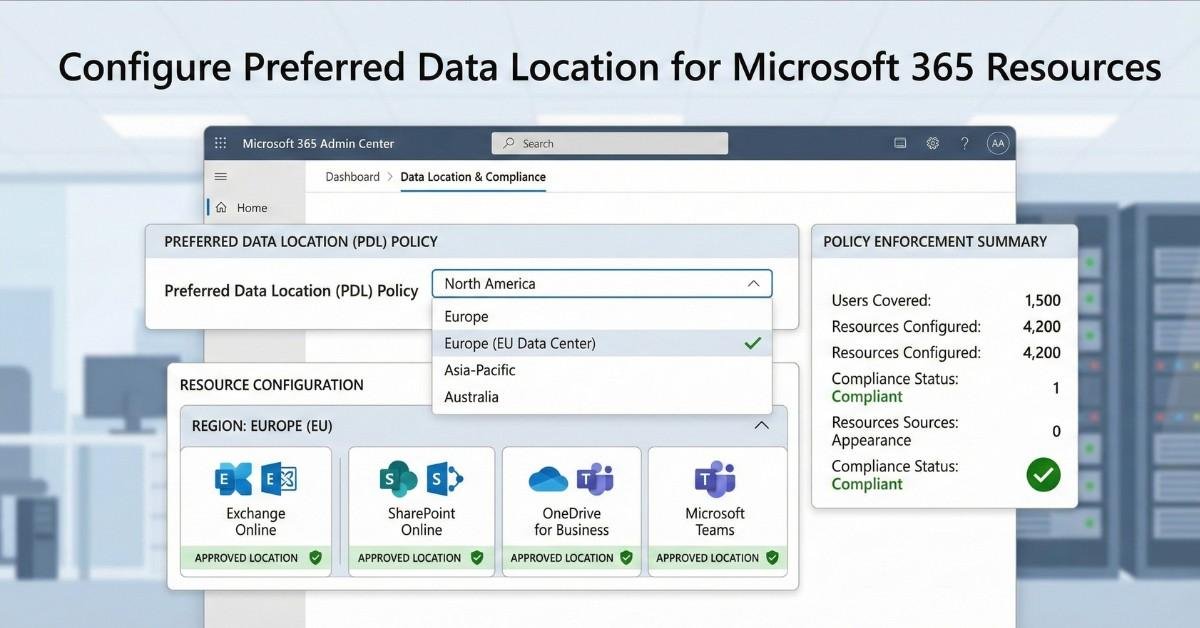
In this topic, I will guide you through the process of configuring the preferred data location office 365 attribute in Microsoft Entra Connect Sync. This attribute is used to specify the geographical location, or region, of a user’s Microsoft 365 data when Multi-Geo capabilities are being utilized. The terms “region” and “geo” are used interchangeably to […]
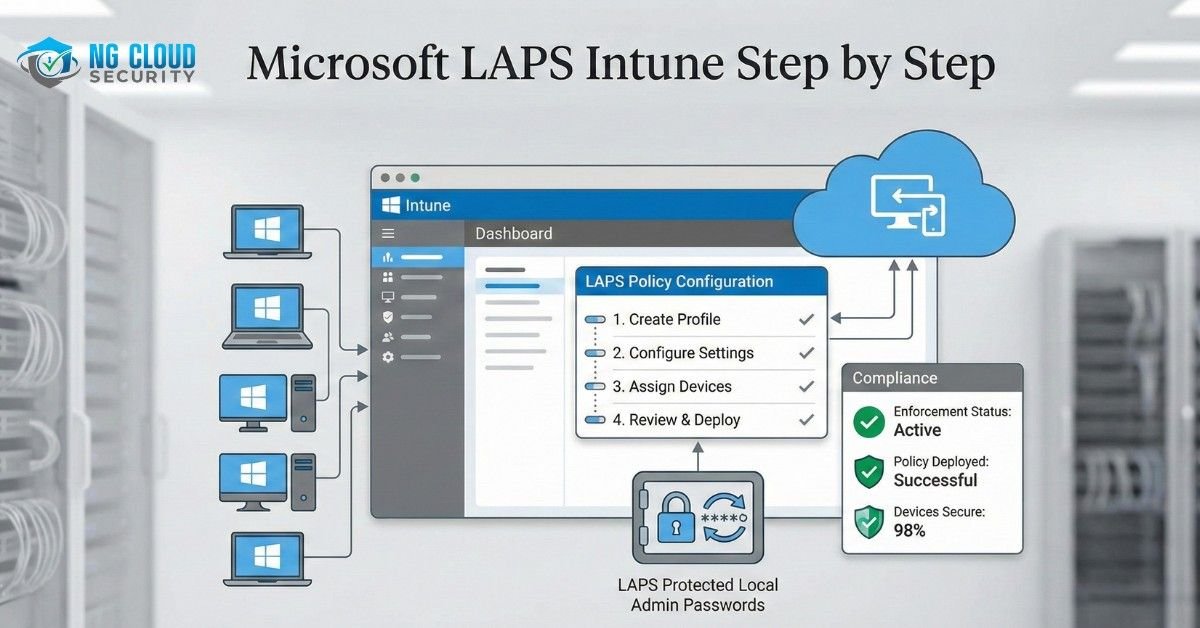
What is Microsoft LAPS? You can easily change the password of your domain administrator account, but what about the local administrator account? The password of the local admin account is often set during installation, but you can’t easily change it on all computers. This is where Windows LAPS comes in. LAPS stands for Local Administrator […]
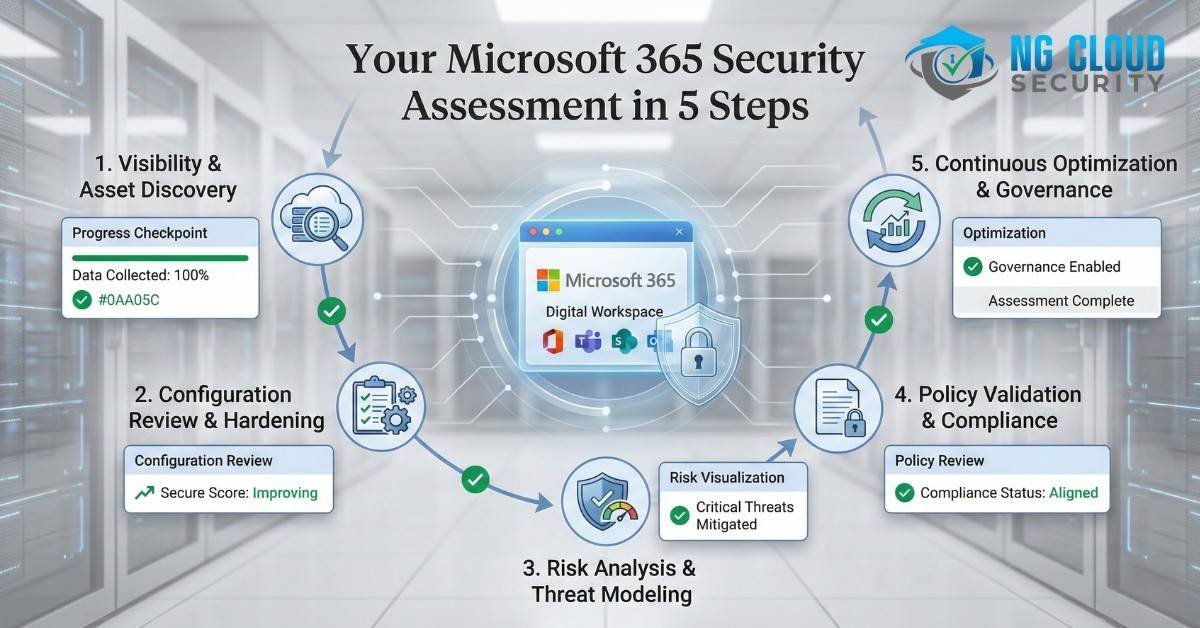
1. Define Objectives and Scope 2. Evaluate Current Security Configuration 3. Assess Threat Landscape and Risks 4. Conduct Vulnerability Analysis 5. Develop Recommendations and Remediation Plan
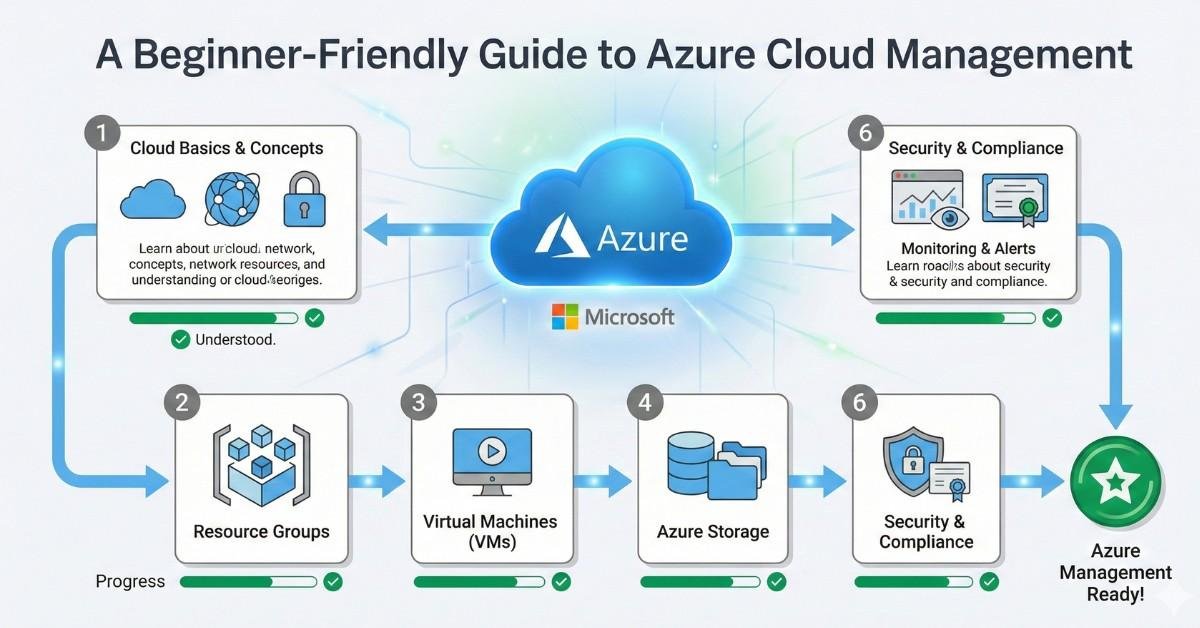
Managing cloud infrastructure can be overwhelming, especially for businesses just beginning their cloud journey. Microsoft Azure offers a robust set of services to help you deploy, manage, and scale your workloads but without a clear strategy, this can lead to higher costs, reduced visibility, and increased security risks. In this guide, NG Cloud Security walks you through […]
In today’s ever-evolving digital landscape, staying ahead of cyber threats requires more than just advanced tools, it demands intelligent, AI-driven solutions. Microsoft Security Copilot is one such innovation that’s transforming how businesses detect, investigate, and respond to cyber threats in real-time. Built on the power of generative AI and integrated deeply into Microsoft’s security ecosystem, Security Copilot […]
In today’s hyper-connected digital landscape, cyber threats are more advanced, persistent, and damaging than ever before. Traditional security tools often operate in silos, leading to fragmented visibility, slow response times, and increased risk exposure. To combat this challenge, organizations are turning to Microsoft Defender for XDR (Extended Detection and Response) a unified cybersecurity solution that centralizes and simplifies […]
Microsoft 365 is a powerful suite of cloud-based productivity and collaboration tools used by over a million organizations globally. With apps like Teams, SharePoint, Exchange Online, OneDrive, and the Power Platform, Microsoft 365 helps businesses streamline operations, enhance team collaboration, and work securely from anywhere. But many companies only scratch the surface of what Microsoft […]
n today’s dynamic digital landscape, streamlined communication, secure data access, and real-time collaboration are critical to business success. Microsoft 365, now known as Microsoft 365, offers a comprehensive suite of productivity and collaboration tools that enable organizations to work smarter and faster. At NG Cloud Security, we specialize in Microsoft 365 integration services that empower your teams to […]
In an era where cyberattacks occur every 39 seconds, securing every access point to your network is more critical than ever. Endpoint security is a modern cybersecurity approach that safeguards every device known as an endpoint that connects to your corporate network. Whether it’s a laptop, mobile phone, or IoT device, NG Cloud Security helps […]