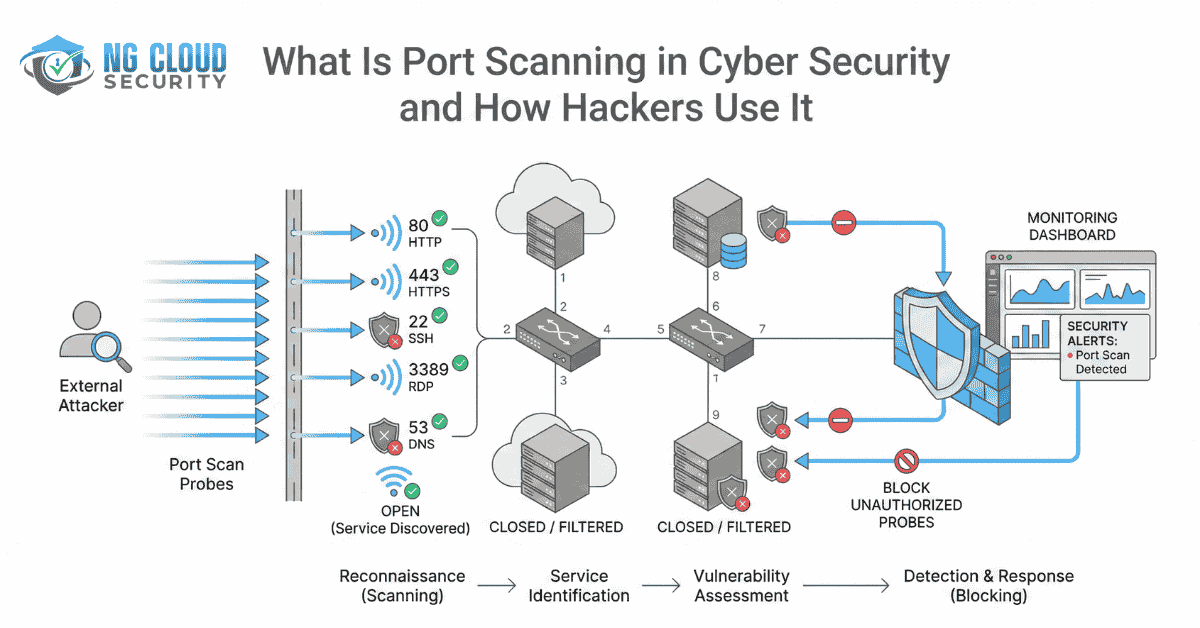
If you are searching for what is port scanning in cyber security, you are already thinking like a security leader. Port scanning is one of the most common reconnaissance techniques used in modern cyber attacks. It is often the first step attackers take before attempting to exploit a system. From my experience working with organizations […]
Endpoint security has evolved rapidly over the past decade. As organizations move to cloud platforms, remote work models, and mobile devices, protecting endpoints has become a core pillar of modern cybersecurity. If you are new to this topic, you can also read our detailed guide on what is endpoint security and how it works. Understanding […]
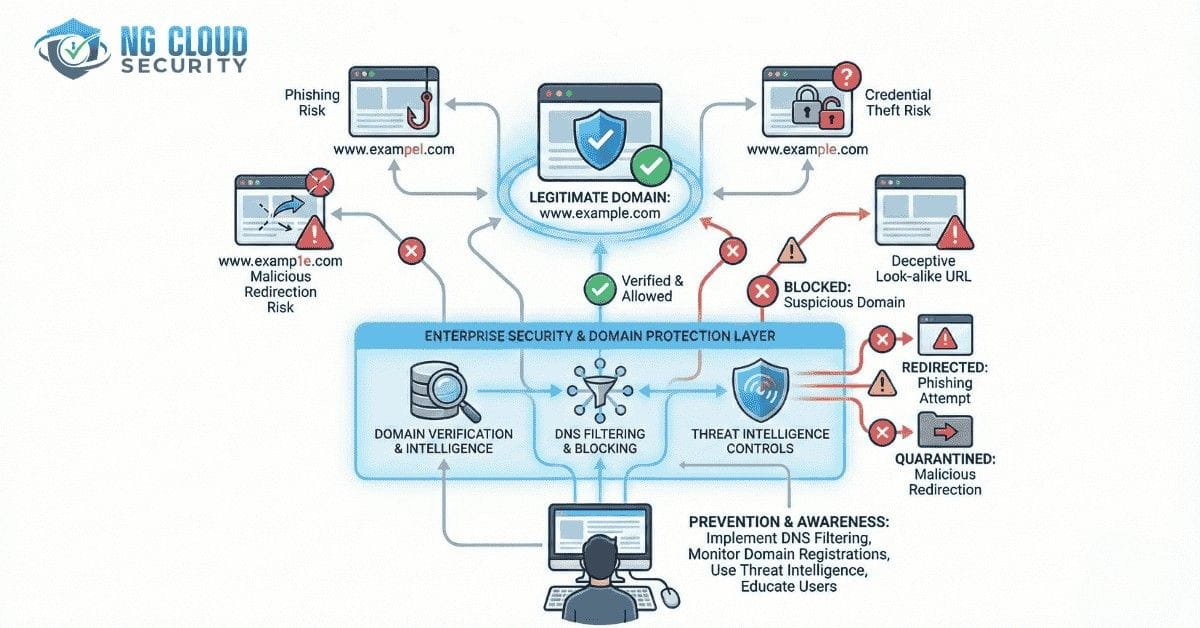
Typosquatting in cyber security is a growing threat that exploits simple human typing errors to steal credentials, distribute malware, and damage brand reputation. While many organizations focus on firewalls and endpoint tools, domain abuse often remains overlooked. In enterprise environments, a single mistyped URL can lead to phishing, account takeover, business email compromise, and regulatory […]
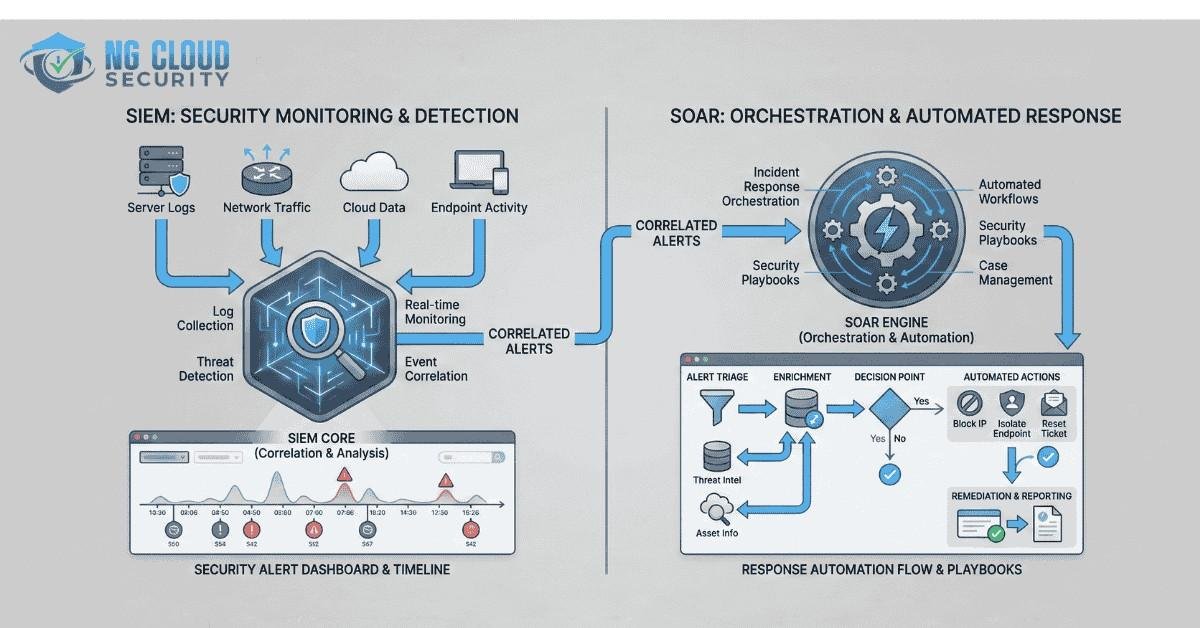
Security teams today are under constant pressure. Alerts are increasing, attack techniques are evolving, and business environments are becoming more complex with cloud adoption, remote work, and regulatory demands. In many organizations, the Security Operations Center acts as the first and last line of defense. One of the most common questions I see security leaders […]
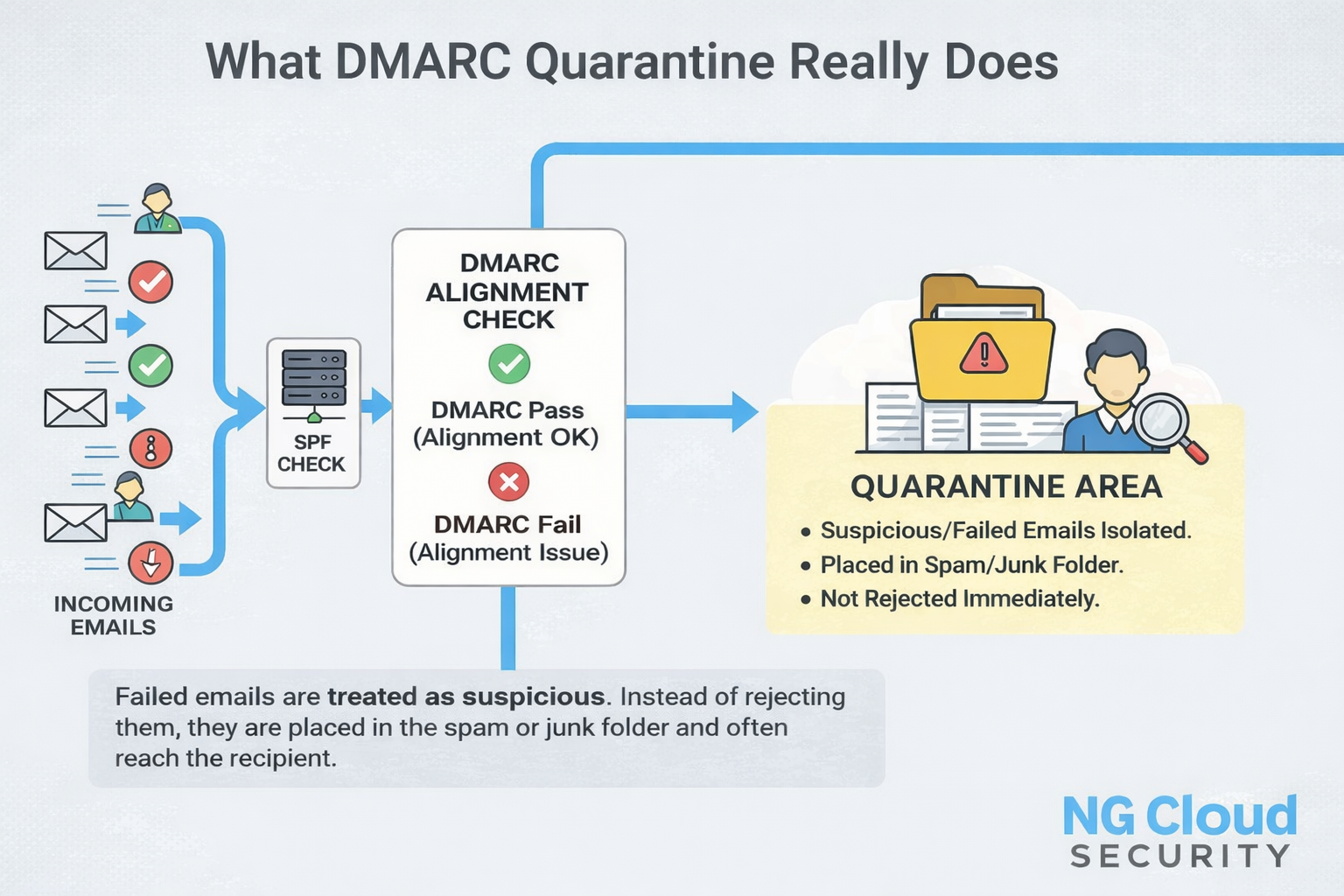
Email remains one of the most trusted channels for business communication, yet it is also one of the most abused. In my experience working with organizations across industries, email authentication issues often surface only after customers report missing invoices or password reset messages. That is usually when DMARC becomes part of the conversation. One of […]
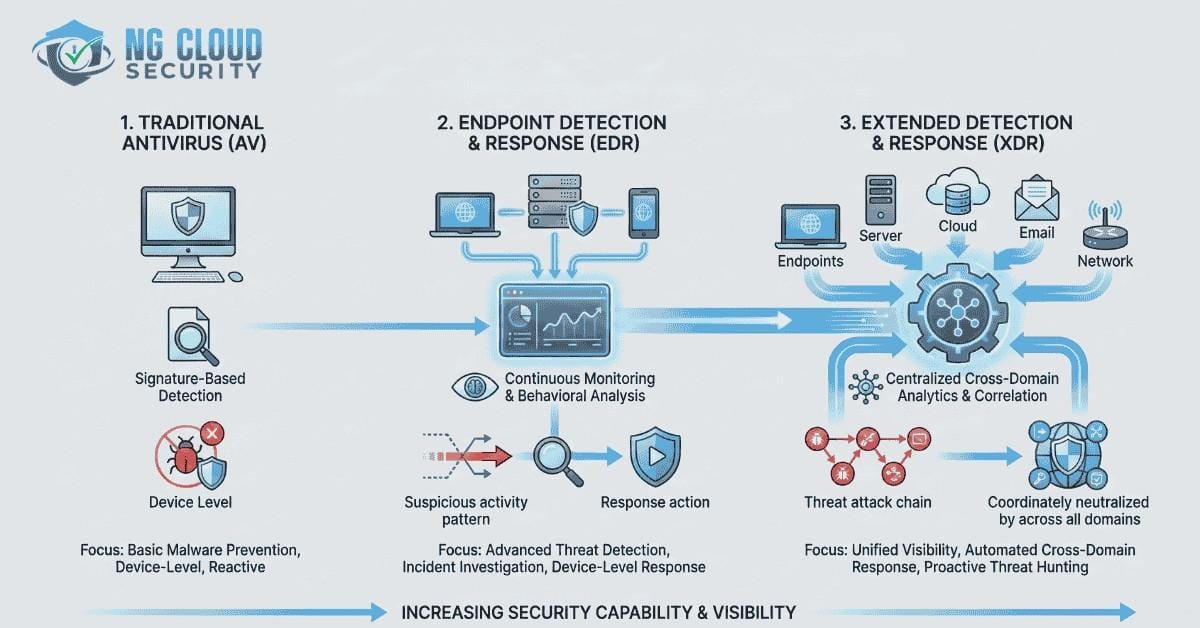
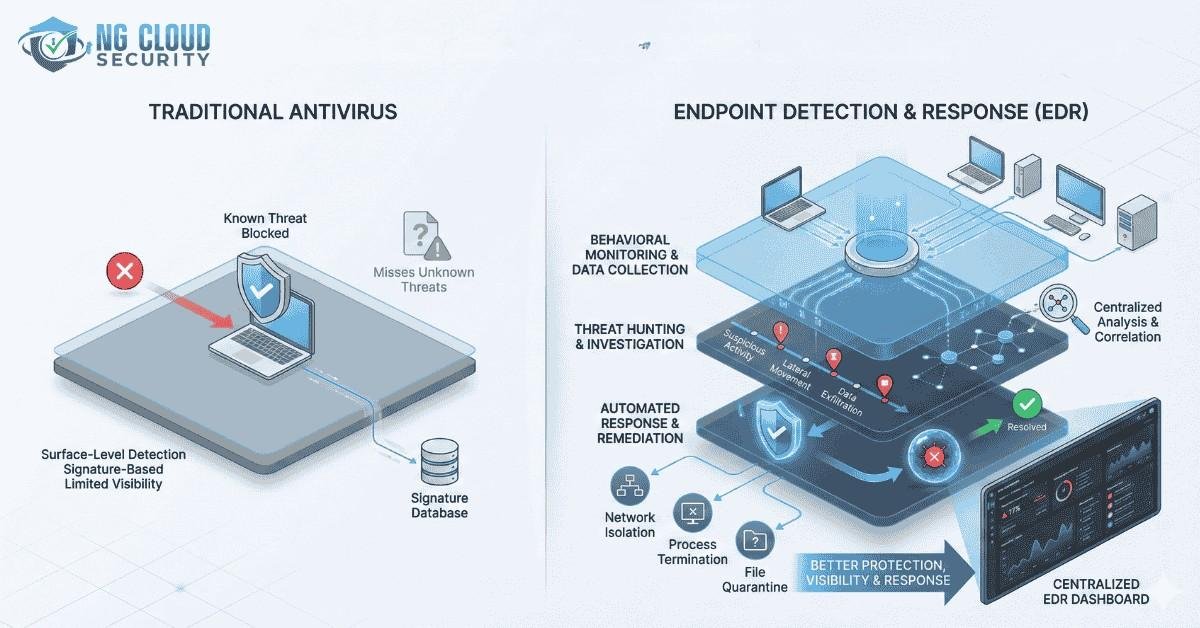
The main difference between EDR and antivirus is one of the most common questions I hear from business owners and IT leaders very frequenlty. Many organizations still depend on traditional antivirus because it feels familiar and safe. Yet the threat landscape has changed faster than most security tools. Attackers no longer behave like the viruses […]
Endpoint security has become a critical part of modern cybersecurity strategy. In my experience working with cloud first and hybrid environments, I have seen how a single endpoint security controller problem can quietly weaken an organization’s defenses. When endpoint visibility breaks, threats often go unnoticed until real damage is done. If you are already investing […]
One of the most common questions I hear from business leaders and IT teams is does Microsoft 365 have a PDF editor. It sounds like a basic requirement, yet it often creates confusion once teams start working with contracts, policies, invoices, and compliance documents inside Microsoft 365. Having worked with Microsoft 365 across different industries, […]
When enterprise leaders ask me how long does cloud migration take, I usually pause before answering. Not because the question is unclear, but because the timeline depends on many moving parts. In real enterprise environments, cloud migration is not a single project. It is a transformation that touches applications, infrastructure, security, compliance, and people. From […]
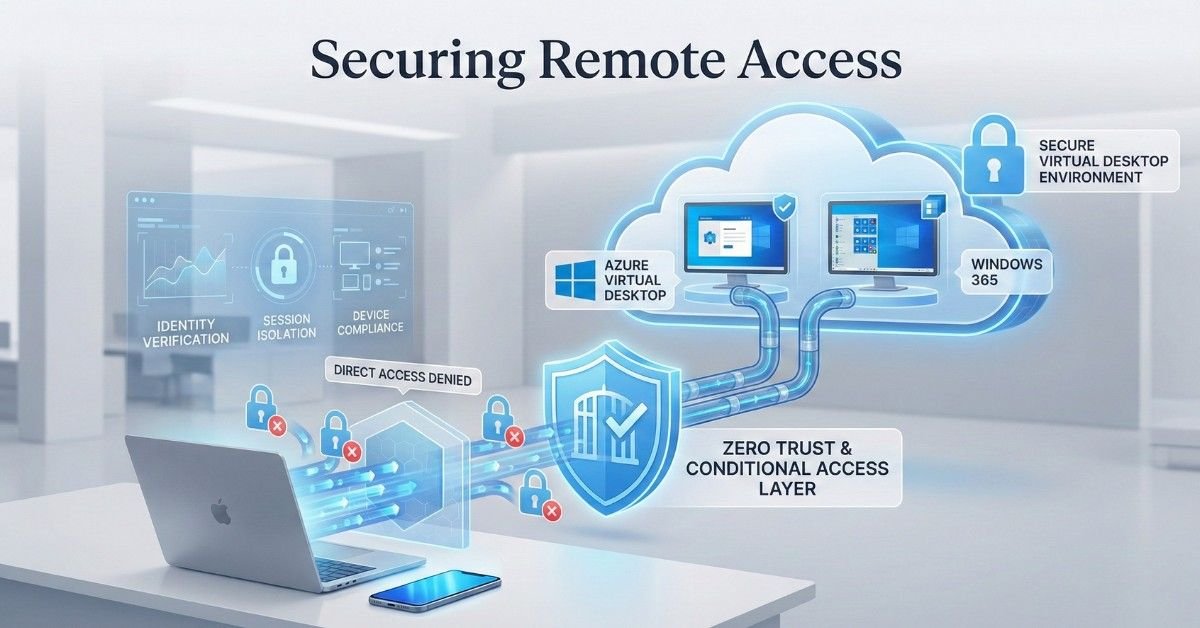
Overview Securing Remote Access is essential when allowing remote users on personal devices to access Azure Virtual Desktop (AVD) and Windows 365 (W365) while restricting access to other cloud applications and organizational data. In this article, we discuss how organizations can safely enable BYOD access without exposing sensitive resources. Securing Azure Virtual Desktop (AVD) plays […]