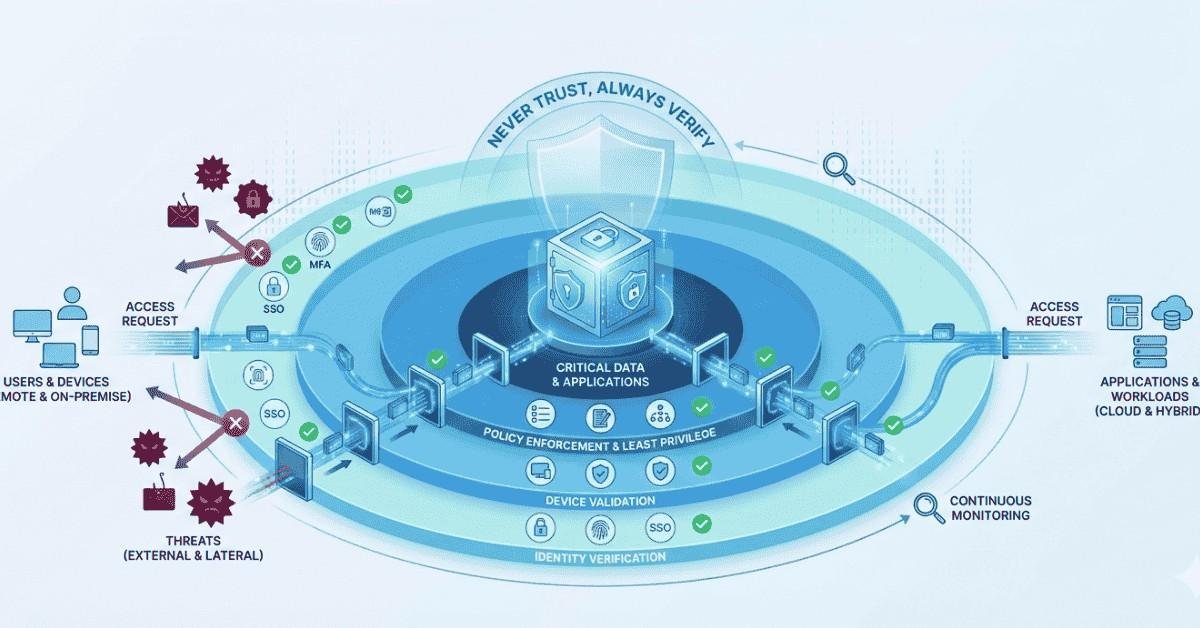
Endpoint security has become a critical part of modern cybersecurity strategy. In my experience working with cloud first and hybrid environments, I have seen how a single endpoint security controller problem can quietly weaken an organization’s defenses. When endpoint visibility breaks, threats often go unnoticed until real damage is done. If you are already investing […]
One of the most common questions I hear from business leaders and IT teams is does Microsoft 365 have a PDF editor. It sounds like a basic requirement, yet it often creates confusion once teams start working with contracts, policies, invoices, and compliance documents inside Microsoft 365. Having worked with Microsoft 365 across different industries, […]
When enterprise leaders ask me how long does cloud migration take, I usually pause before answering. Not because the question is unclear, but because the timeline depends on many moving parts. In real enterprise environments, cloud migration is not a single project. It is a transformation that touches applications, infrastructure, security, compliance, and people. From […]
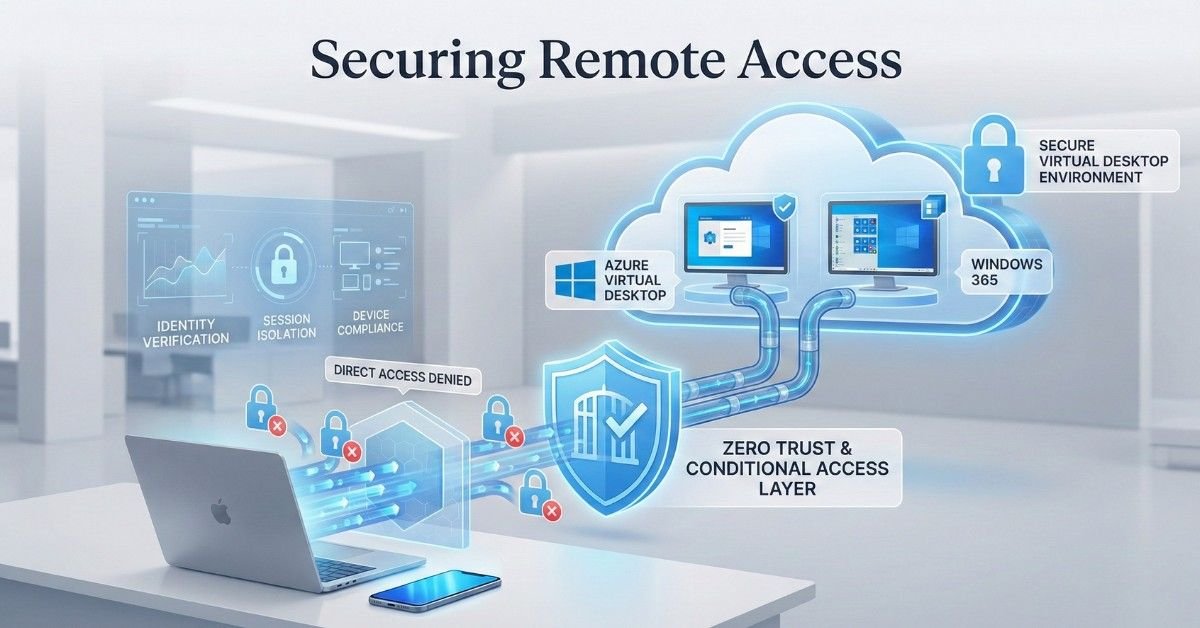
Overview In this article, we will discuss how to allow remote users on personal devices to access Azure Virtual Desktop (AVD) and Windows 365 (W365) while blocking access to all other cloud applications and organizational data. Securing Azure Virtual Desktop (AVD) is crucial for maintaining a secure and compliant environment, especially when enabling remote access […]
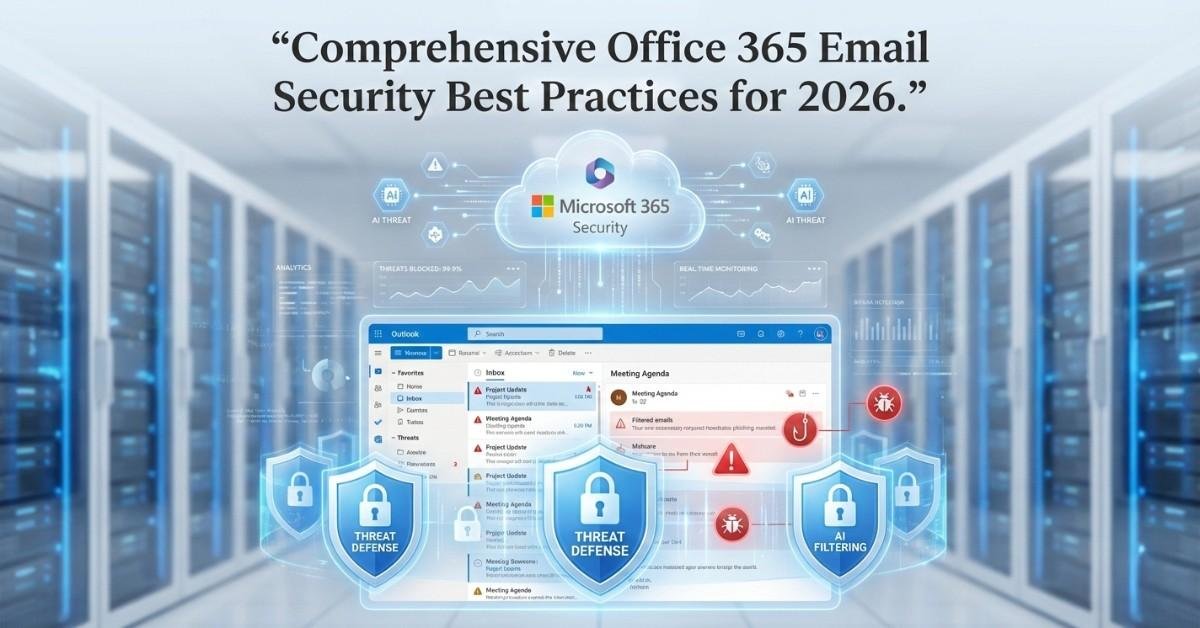
Office 365 Email Security Best Practices Overview Email security is a critical aspect of modern business operations, with email being the primary communication channel for most organizations. Unfortunately, it is also a major target for cyberattacks such as phishing, malware, and business email compromise (BEC). Microsoft Office 365, as one of the most widely used […]
Overview Microsoft Office 365 Advanced Threat Protection (ATP) helps protect your organization from sophisticated threats like phishing, malware, and business email compromise. It is crucial to regularly review and optimize ATP settings to ensure your organization’s security remains strong. The Office 365 ATP Recommended Configuration Analyzer (ORCA) is a PowerShell module designed to evaluate your ATP configuration […]
Overview NG Cloud Security, a proud Microsoft Security Solution Partner, offers comprehensive managed service support designed to meet your IT needs around the clock. Our dedicated support team is available 24×7 to ensure your operations run smoothly and securely. Support Services Offered: 24×7 Dedicated Support Team: Senior Security Solution Team: L1 and L2 IT Support: […]
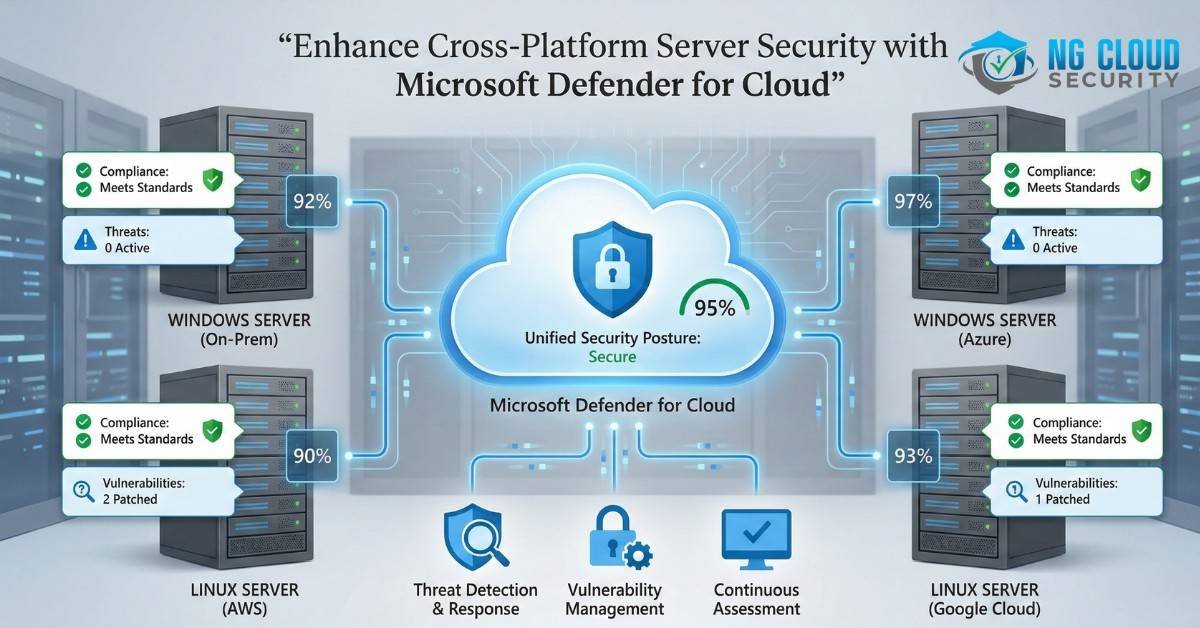
Oerview In today’s multi-cloud, hybrid IT environments, maintaining real-time security and operational efficiency across diverse servers can be challenging. Organizations need robust solutions that offer comprehensive protection with minimal disruption and downtime. Microsoft Defender for Cloud is the answer, providing an integrated security management platform that seamlessly unifies security operations across various infrastructures. Why Choose […]
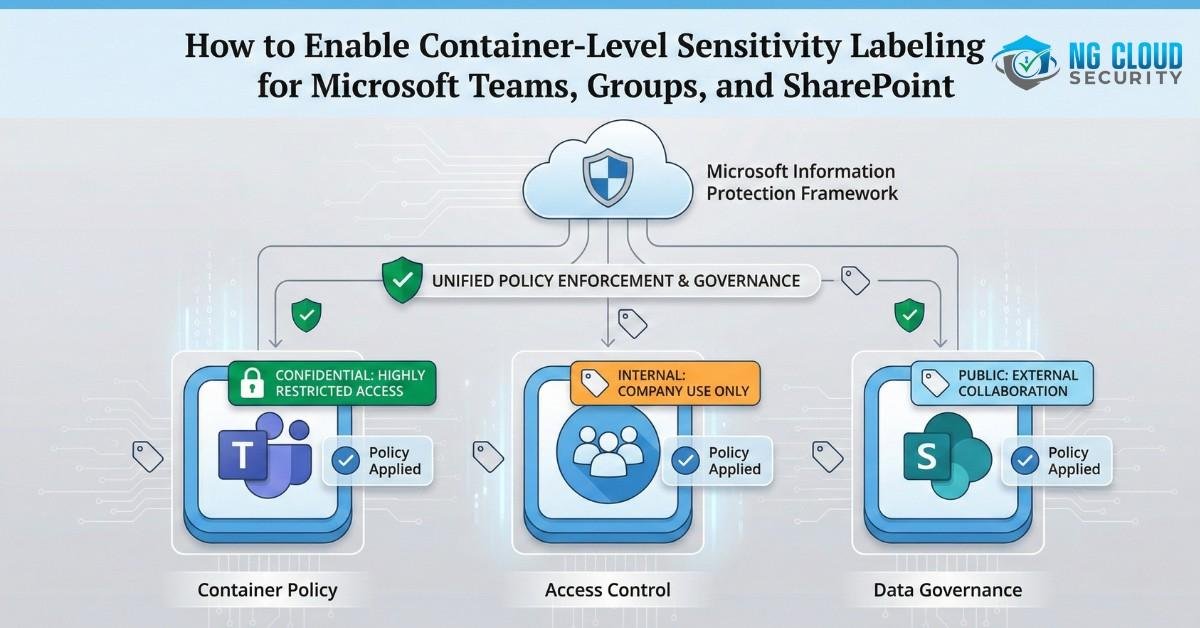
Overview In this article, we will discuss how to enable Microsoft Information Protection (MIP) sensitivity labeling for Microsoft 365 Groups, Teams, and SharePoint Online sites. By default, this setting is disabled on every new Microsoft 365 tenant build. Therefore, when you plan to deploy MIP services for data classification to protect your organization’s data on […]
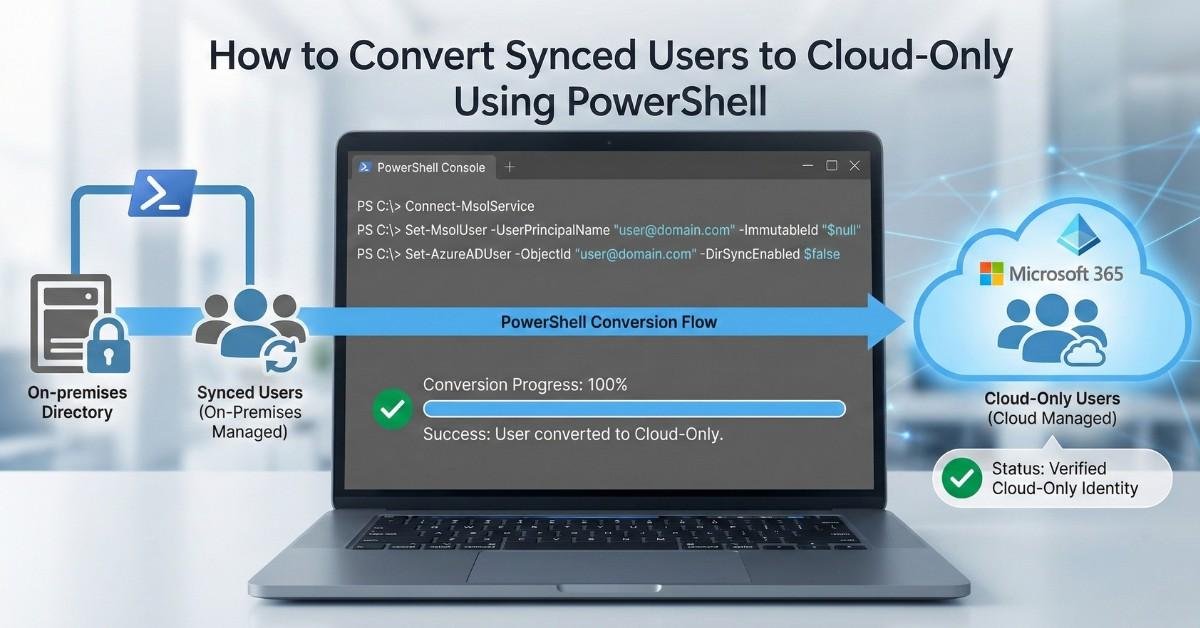
To convert synced user to cloud only using PowerShell, organizations must disable Microsoft Entra ID (Azure AD) directory synchronization. Once synchronization is turned off, Microsoft automatically converts all synced identities into cloud-only users while preserving their existing Microsoft 365 data and permissions. This method is the recommended and supported approach when planning to convert on-prem user to […]