Zero Trust: A New Security Mindset for New Challenges
In today’s digital-first world, cyber threats are no longer limited to external attacks. Insider threats, credential theft, and supply chain vulnerabilities have become equally dangerous. Traditional perimeter-based security models that rely on the concept of “trust but verify” are proving inadequate. That’s where Zero Trust security solutions come in — a revolutionary approach that challenges the very foundation of conventional network security.
NG Cloud Security brings this advanced model to life with cutting-edge solutions designed to secure modern enterprises from evolving threats. Let’s explore how adopting the Zero Trust network architecture can transform your cybersecurity posture for today’s challenges.
What is Zero Trust Security?
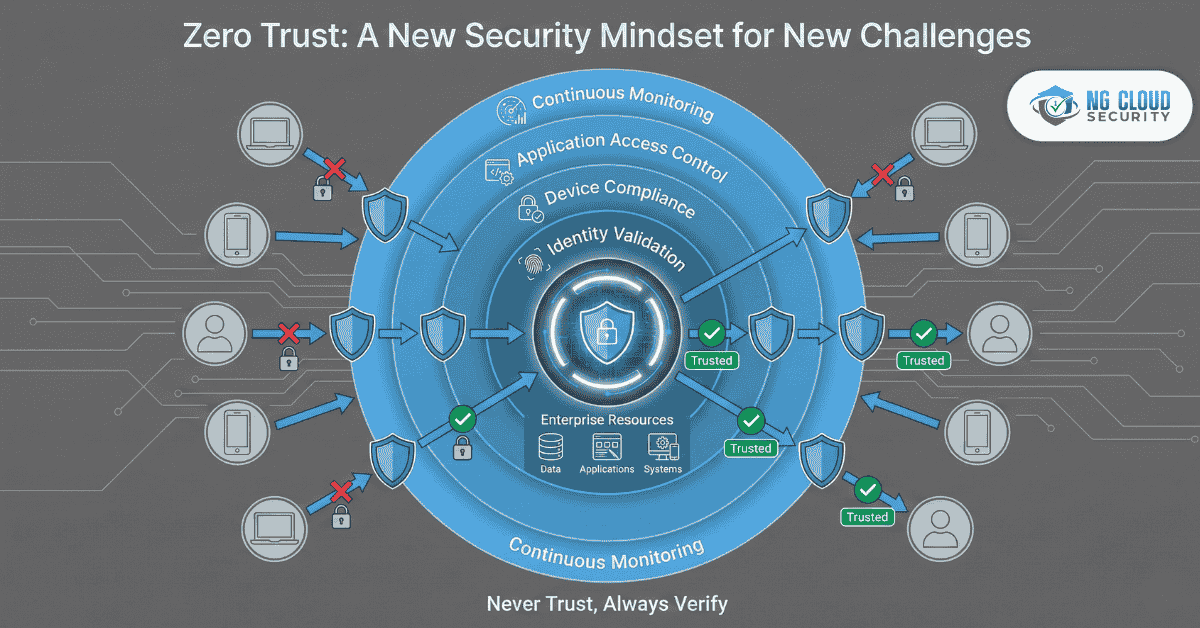
Zero Trust is not just a technology — it’s a security mindset. It operates on the principle of “never trust, always verify.” No user or device, whether inside or outside the organization, is automatically trusted. Every access request must be authenticated, authorized, and continuously validated before granting access to resources.
Zero Trust security solutions create a unified framework that ensures every layer of your digital ecosystem — from network and applications to users and data — is verified and monitored.
The Core Pillars of Zero Trust
Here’s a breakdown of each pillar:
1. Zero Trust Network Architecture
A Zero Trust network architecture eliminates implicit trust within the network. Instead of relying on firewalls or VPNs to secure the perimeter, it assumes every connection could be compromised. Access is segmented based on policies that restrict movement within the network.
This architecture ensures that even if a cyber attacker gains access to one part of the network, they cannot move laterally to other systems or steal sensitive data. NG Cloud Security designs robust Zero Trust architectures customized to the organization’s infrastructure, ensuring maximum visibility and control.
2. Identity and Access Management (IAM)
Identity is the cornerstone of Zero Trust security solutions. Modern Identity and Access Management (IAM) systems go beyond passwords — they validate who is accessing, what they’re accessing, and how they’re doing it.
With NG Cloud Security’s IAM solutions, organizations can implement strict access policies using:
- Multi-Factor Authentication (MFA)
- Role-Based Access Control (RBAC)
- Privileged Access Management (PAM)
- Adaptive access policies based on context and device health
This ensures that only legitimate users and devices gain access to critical resources, significantly reducing the risk of data breaches.
3. Microsegmentation Security Model
The microsegmentation security model is at the heart of the Zero Trust approach. It divides the network into small, isolated segments, each protected by strict access controls.
With micro segmentation, even if one part of the network is compromised, the damage remains contained. Attackers can’t easily move across systems or access unrelated resources. NG Cloud Security leverages micro segmentation to enhance network visibility and reduce attack surfaces, ensuring every data flow is monitored and secured.
4. Continuous Authentication and Verification
Unlike traditional models that verify credentials once during login, Zero Trust security solutions use continuous authentication and verification.
This means user identities, devices, and sessions are constantly evaluated based on:
- User behavior analytics
- Device compliance status
- Network activity patterns
If any anomaly is detected, access is restricted or revoked in real time. NG Cloud Security integrates intelligent monitoring tools and AI-driven analytics to enable proactive threat detection and immediate response to suspicious activity.
5. Zero Trust Data Protection Framework
At the core of Zero Trust lies the principle of protecting data everywhere. The Zero Trust data protection framework ensures data confidentiality, integrity, and availability across all environments — on-premises, in the cloud, and at endpoints.
This framework includes encryption, data classification, and secure sharing mechanisms to prevent unauthorized access or data loss. With NG Cloud Security’s Zero Trust implementation, businesses can enforce data protection policies that align with regulatory compliance standards such as GDPR, HIPAA, and ISO 27001.
Why Businesses Need Zero Trust Security Solutions
The growing sophistication of cyber threats, coupled with the shift toward hybrid work environments, demands a new approach to security. Here’s why enterprises are adopting Zero Trust security solutions from NG Cloud Security:
- Enhanced Security Posture: Reduces risks from internal and external threats through least-privilege access.
- Improved Visibility: Enables detailed monitoring of user activity and network traffic.
- Compliance Assurance: Meets regulatory data protection standards effectively.
- Scalability: Easily adapts to cloud-native and hybrid infrastructure models.
- Resilience Against Attacks: Limits attack surfaces and prevents lateral movement within the network.
By integrating Zero Trust network architecture and micro segmentation security models, organizations can achieve complete control over who accesses their resources and how.
Advantage
NG Cloud Security specializes in delivering enterprise-grade Zero Trust security solutions that combine technology, automation, and expert-driven strategy. Their offerings include:
- End-to-end Zero Trust assessments and design
- Advanced IAM and privilege management integration
- Cloud-native microsegmentation deployments
- Real-time monitoring and continuous verification systems
- Comprehensive Zero Trust data protection frameworks
Whether your organization is modernizing its IT infrastructure or moving workloads to the cloud, NG Cloud Security provides customized solutions to ensure security at every layer of your digital environment.
FAQ’s
Author
Devendra Singh
Hi, I'm Founder & Chief Security Architect at NG Cloud Security, a leading Managed Security Service Provider and Cloud Solution Partner. With over a decade of experience advising global organizations, he helps leaders navigate digital transformation while balancing security, compliance, and business goals. Working with clients across Asia, Europe, and the US, Devendra Singh delivers Zero Trust–aligned cloud and IT strategies, from risk assessments to multi-cloud implementation and optimization, driving stronger security, operational efficiency, and measurable business growth.