Typosquatting in Cyber Security: Risks, Techniques, and Prevention
Typosquatting in cyber security is a growing threat that exploits simple human typing errors to steal credentials, distribute malware, and damage brand reputation. While many organizations focus on firewalls and endpoint tools, domain abuse often remains overlooked.
In enterprise environments, a single mistyped URL can lead to phishing, account takeover, business email compromise, and regulatory exposure. Typosquatting is not just a consumer problem. It is a business risk that directly impacts security, compliance, and trust.
If you are strengthening your overall cloud security strategy, protecting your domain ecosystem must be part of that framework.
What Is Typosquatting in Cyber Security
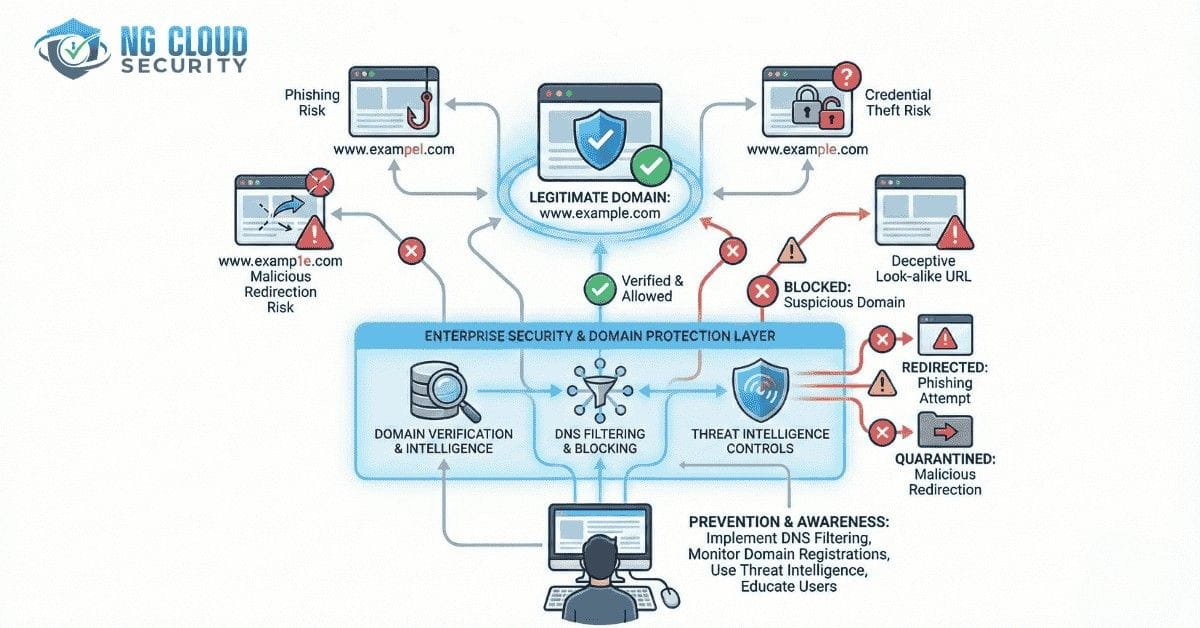
Typosquatting in cyber security refers to the practice of registering domain names that closely resemble legitimate websites but contain minor spelling errors or character variations. Attackers rely on common typing mistakes to redirect users to malicious domains.
It is also known as URL hijacking, domain mimicry, or brand impersonation.
Users typically land on typosquatted sites in two ways:
- Accidentally mistyping a domain name
- Clicking a phishing link that looks legitimate
Once on the fake site, users may unknowingly enter login credentials, payment details, or download malicious software.
How Typosquatting Works
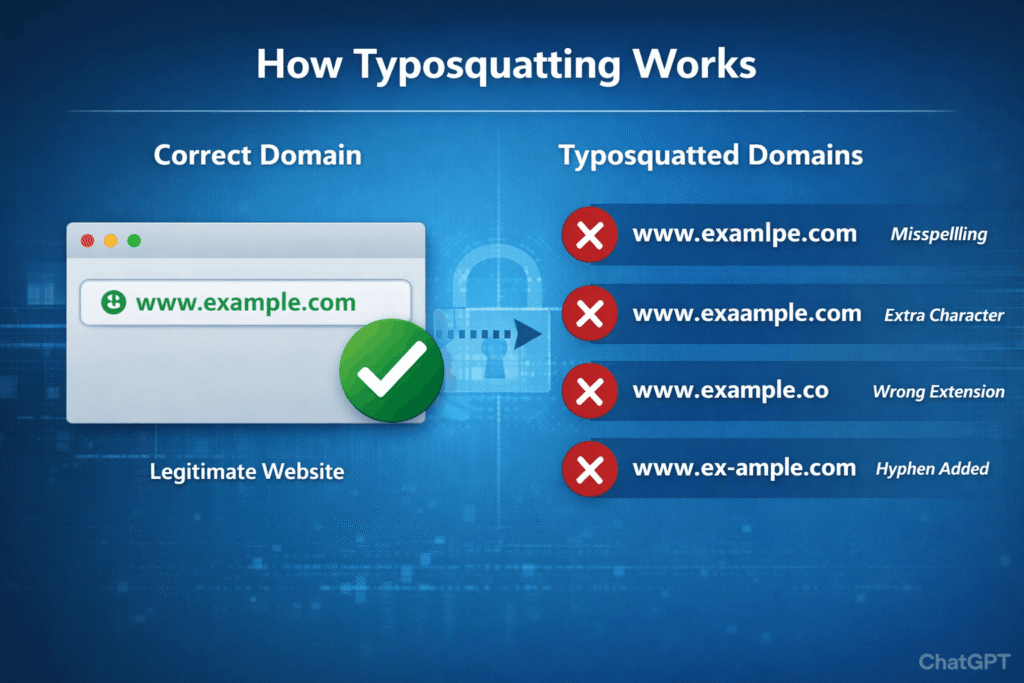
The attack begins when a cybercriminal registers a misspelled version of a trusted domain. Examples include:
- Character omission such as example instead of example
- Character duplication such as example
- Character substitution such as replacing letter o with zero
- Incorrect domain extension such as .co instead of .com
- Hyphen manipulation by adding or removing hyphens
Attackers then design the fake website to mirror the original brand including logos and page layouts.
These campaigns are often combined with email phishing, which is why strong email security controls are critical in preventing credential harvesting.
Combosquatting vs Typosquatting
A related technique called combosquatting does not rely on spelling errors. Instead, attackers register domains that include a legitimate brand name plus additional words.
Examples include brand secure login or brand account verification.
There is no typo involved, but the extra words create urgency and trust. Combosquatting is frequently used in cloud credential phishing and supplier fraud attacks.
Typosquatting vs Cybersquatting
Although the terms are often confused, they are different.
Cybersquatting involves registering a brand related domain with the intention of selling it back to the legitimate owner for profit.
Typosquatting focuses on exploiting user errors for phishing, malware distribution, traffic monetization, or identity theft.
Typosquatting is operationally malicious, while cybersquatting is typically financially opportunistic.
Enterprise Risks of Typosquatting in Cyber Security
Typosquatting can have serious consequences for organizations.
Credential Theft and Account Takeover
Fake login portals capture usernames and passwords. If multi factor authentication is not enforced through proper identity and access management, attackers may gain full access to enterprise systems.
Business Email Compromise
Attackers impersonate vendors or executives using lookalike domains. This can result in fraudulent payments and financial loss.
Drive By Malware Downloads
Some typosquatted sites trigger malicious scripts automatically when visited. These drive-by downloads can install spyware, ransomware, or remote access tools without user awareness.
Organizations investing in endpoint security solutions significantly reduce execution risk.
Brand and Compliance Damage
When customers fall victim to malicious domains, trust erodes. In regulated industries, data exposure can also trigger compliance penalties.
A proactive cloud security assessment helps identify exposure gaps related to domain abuse and external threats.
Real World Examples of Typosquatting
Several well known brands have been targeted through domain variations designed to capture traffic. In high traffic seasons such as elections, product launches, or financial reporting periods, attackers register hundreds of lookalike domains to exploit public attention.
Financial institutions, ecommerce platforms, and SaaS providers are frequent targets because stolen credentials have high resale value on underground markets.
How to Prevent Typosquatting Attacks
A layered defense strategy is essential.
Register Domain Variations
Secure common misspellings of your primary domain and redirect them to your official site.
Monitor Domain Registrations
Continuously track newly registered domains that resemble your brand.
Strengthen Email Authentication
Proper SPF, DKIM, and DMARC implementation prevents spoofed domains from reaching user inboxes. This complements your broader email phishing protection strategy
Deploy DNS Filtering and Threat Detection
Advanced monitoring through SOC managed services can identify suspicious domain behavior and block malicious traffic early.
Enforce Zero Trust Architecture
Adopting a Zero Trust security framework ensures that even if credentials are stolen, attackers cannot move freely within the environment.
Conduct Employee Awareness Training
Educate employees to verify URLs carefully and avoid clicking suspicious links.
Legal Protection Against Typosquatting
Organizations can challenge fraudulent domains through dispute resolution mechanisms such as the Uniform Domain Name Dispute Resolution process. Trademark monitoring services also help track brand abuse.
Legal response combined with proactive monitoring reduces long term domain risk.
Typosquatting Prevention Checklist
- Register common domain misspellings
- Monitor similar domain registrations
- Implement multi factor authentication
- Deploy DNS filtering
- Configure DMARC policies
- Use endpoint protection tools
- Adopt Zero Trust access controls
- Educate employees regularly
Frequently Asked Questions About Typosquatting in Cyber Security
Is typosquatting illegal
In many jurisdictions, registering a domain to impersonate a brand or conduct fraud is illegal, especially when trademark violations or phishing are involved.
Can typosquatting install malware
Yes. Some typosquatted domains execute drive-by downloads that silently install malicious software.
How do companies stop typosquatting
Companies combine domain monitoring, defensive domain registration, email authentication, DNS filtering, and Zero Trust identity controls.
What is combosquatting
Combosquatting involves adding extra words to a legitimate brand domain to create deceptive but convincing malicious domains.
Final Thoughts
Typosquatting in cyber security is a silent yet highly effective attack vector. It exploits human behavior rather than technical vulnerabilities. For enterprises, the consequences include credential theft, financial fraud, regulatory exposure, and brand damage.
Modern organizations must treat domain security as part of their broader cyber resilience strategy. When integrated with cloud security, identity governance, endpoint protection, and continuous SOC monitoring, the risk can be significantly reduced.
Security is not just about defending infrastructure. It is about protecting trust at every digital touchpoint. By proactively addressing typosquatting risks, organizations strengthen both their security posture and long term credibility.