SOAR vs SIEM: Which Security Platform Does Your SOC Need?
Security teams today are under constant pressure. Alerts are increasing, attack techniques are evolving, and business environments are becoming more complex with cloud adoption, remote work, and regulatory demands. In many organizations, the Security Operations Center acts as the first and last line of defense.
One of the most common questions I see security leaders struggle with is SOAR vs SIEM. Both platforms promise better visibility, faster response, and stronger security posture. Yet they solve very different problems. Choosing the wrong one, or deploying them in the wrong order, often leads to alert fatigue, slow response times, and frustrated analysts.
This blog breaks down SOAR vs SIEM in a practical way, based on real operational needs rather than marketing promises.
What Is a SIEM Platform
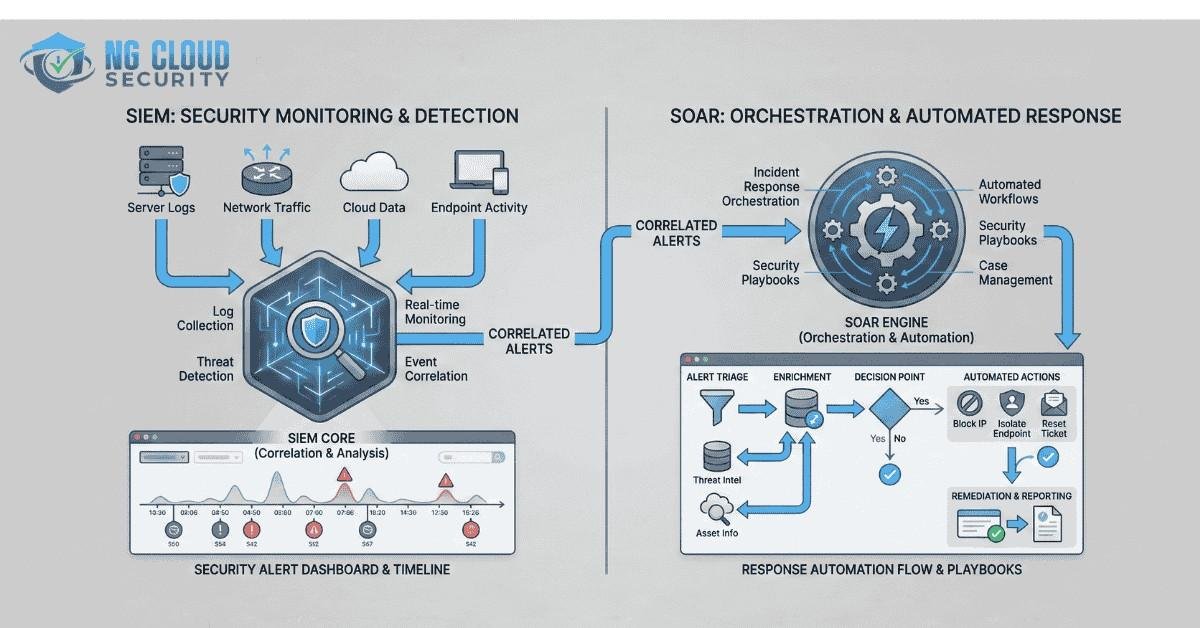
A SIEM platform focuses on collecting, correlating, and analyzing security data from across your environment. This includes logs from endpoints, servers, cloud workloads, firewalls, identity systems, and SaaS applications.
At its core, SIEM provides centralized visibility. Instead of jumping between multiple tools, analysts can view security events in one place and understand what is happening across the organization.
Key Capabilities of SIEM
SIEM platforms excel at log aggregation and correlation. They normalize data from different sources and apply detection rules to identify suspicious behavior. Over time, this helps security teams identify trends, investigate incidents, and meet compliance requirements.
In my experience, SIEM becomes essential as soon as an organization starts scaling cloud workloads or operating across multiple regions. Without centralized logging, investigations turn into guesswork.
For organizations using Microsoft security tooling, platforms like Microsoft Sentinel play a major role in SIEM strategy. You can explore how this fits into modern operations on the Microsoft Sentinel
What Is a SOAR Platform
SOAR stands for Security Orchestration Automation and Response. While SIEM focuses on visibility, SOAR focuses on action.
SOAR platforms automate repetitive security tasks, orchestrate workflows across multiple tools, and guide analysts through structured response processes. Instead of manually triaging every alert, SOAR allows teams to respond faster and more consistently.
Core Strengths of SOAR
SOAR shines when alert volume becomes overwhelming. It automates enrichment, ticket creation, user notification, and even containment actions like disabling accounts or isolating endpoints.
From what I have seen in real SOC environments, SOAR is often introduced after teams realize that visibility alone does not reduce risk. Speed and consistency matter just as much as detection.
SOAR is especially valuable in organizations offering or consuming SOC managed services, where response time and operational efficiency directly impact service quality. This aligns closely with managed SOC operations.
SOAR vs SIEM: Core Differences Explained
Understanding SOAR vs SIEM becomes easier when you compare their primary purpose.
| Aspect | SIEM | SOAR |
| Primary role | Centralized security visibility and detection | Automated response and workflow execution |
| Focus area | Log collection and correlation | Incident response and orchestration |
| Type of work | Data driven analysis | Process driven automation |
| Alert handling | Generates and prioritizes alerts | Acts on alerts using playbooks |
| Analyst involvement | High manual investigation effort | Reduced manual effort through automation |
| Value delivered | Awareness and compliance readiness | Speed, consistency, and efficiency |
How SIEM Supports Compliance and Visibility
One area where SIEM clearly stands out is compliance. Many regulatory frameworks require centralized logging, audit trails, and long term data retention.
SIEM platforms help organizations demonstrate compliance by maintaining searchable logs and detailed incident timelines. This becomes critical during audits, investigations, and regulatory reporting.
Organizations undergoing security assessments or compliance validation often rely heavily on SIEM capabilities. This aligns well with structured security assessment services
How SOAR Improves SOC Efficiency
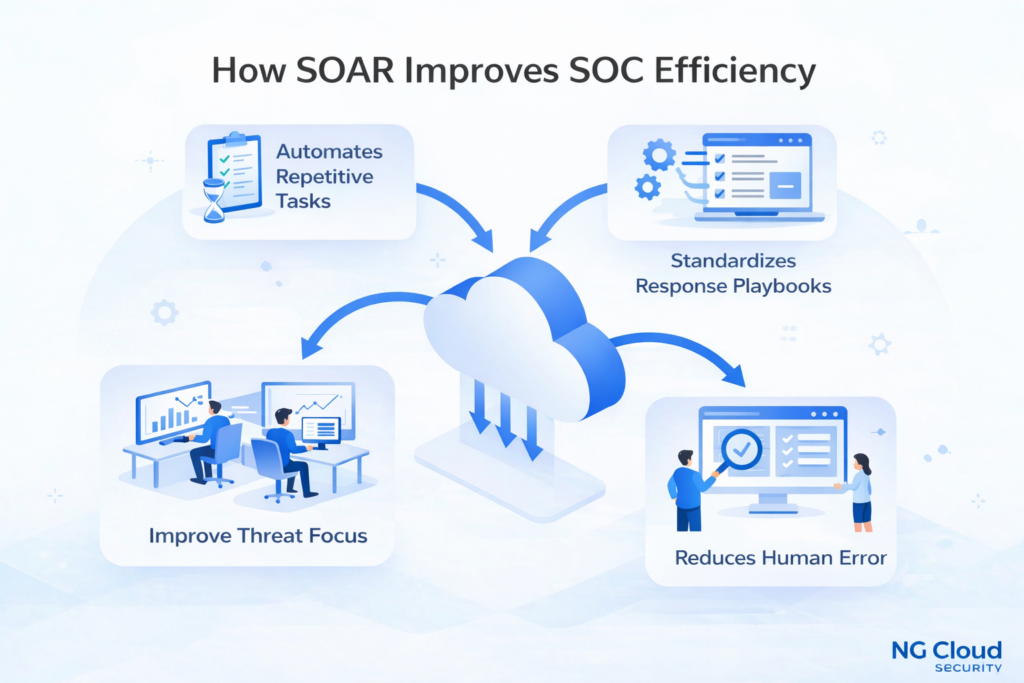
While SIEM improves visibility, SOAR improves efficiency. Security teams often waste valuable time on repetitive tasks like log enrichment, IP reputation checks, or manual ticket updates.
SOAR removes this friction. It standardizes response actions and reduces human error. Junior analysts can follow guided workflows, while senior analysts focus on complex threats.
In my experience, SOC maturity increases significantly once automation is introduced thoughtfully. The key is to automate the right tasks without losing human oversight.
When You Need SIEM First
For organizations building or modernizing their SOC, SIEM usually comes first. Without reliable data and correlation, automation has nothing meaningful to act on.
You need SIEM if you lack centralized visibility, struggle with incident investigation, or cannot meet compliance requirements. SIEM is also critical in cloud heavy environments where logs are distributed across multiple platforms.
Organizations adopting Zero Trust security models often rely on SIEM to correlate identity, endpoint, and network signals. This ties closely to Zero Trust security services.
When SOAR Becomes Essential
SOAR becomes essential when alert volume outpaces human capacity. If analysts are drowning in alerts, response times increase and critical threats may be missed.
SOAR is ideal for mature SOCs that already have defined playbooks and stable detection logic. Automation without process clarity often leads to chaos rather than efficiency.
SOAR also adds value in environments using multiple security tools, where orchestration reduces tool sprawl and operational friction.
SOAR vs SIEM in Modern Cloud Environments
Cloud environments introduce new challenges for security operations. Logs are dynamic, workloads scale rapidly, and traditional perimeter defenses no longer apply.
SIEM helps aggregate signals from cloud infrastructure, identity systems, and SaaS platforms. SOAR then automates responses such as access revocation or workload isolation.
| Security Use Case | SIEM Capability | SOAR Capability |
| Detecting suspicious logins | Strong | Limited |
| Correlating multi source events | Strong | Depends on SIEM |
| Automating phishing response | Basic | Strong |
| Compliance reporting | Strong | Limited |
| Incident response execution | Manual | Automated |
| SOC workload reduction | Limited | High |
For organizations investing in cloud security strategy, both platforms play complementary roles. This approach aligns well with broader cloud security initiatives.
Do You Need SOAR and SIEM Together
The real answer to SOAR vs SIEM is that most mature SOCs eventually need both.
SIEM provides detection and context. SOAR provides speed and consistency. Together, they create a scalable security operations model.
However, deploying both without a roadmap often leads to wasted investment. Start with SIEM to build visibility and detection maturity. Introduce SOAR once processes are defined and alert quality is stable.
When SIEM or SOAR Makes More Sense
| Scenario | Better Choice |
| No centralized logging | SIEM |
| High false positive alerts | SIEM with tuning |
| Repetitive incident handling | SOAR |
| Limited SOC staff | SOAR |
| Regulatory compliance needs | SIEM |
| Large scale cloud environment | SIEM and SOAR |
Final Thoughts on SOAR vs SIEM
Choosing between SOAR vs SIEM is not about features. It is about operational reality. Security tools should support people, not overwhelm them.
In my experience, successful SOCs focus on fundamentals first. Visibility, context, and detection accuracy come before automation. Once those foundations are in place, SOAR becomes a force multiplier rather than a complexity layer.
If your SOC is struggling with blind spots, start with SIEM. If your SOC is struggling with speed and scale, SOAR is the next step. And if you are aiming for long term resilience, plan for both working together.