Defender for XDR Cyber Defense
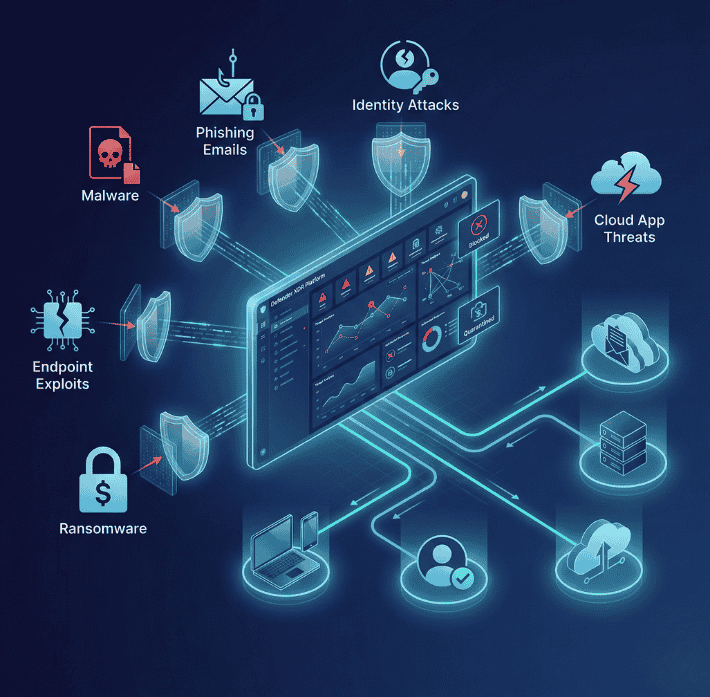
Defender XDR security plays a critical role in protecting modern organizations from increasingly complex cyber threats. NG Cloud Security’s Defender for XDR services provide comprehensive protection against malware, phishing attacks, ransomware, and advanced persistent threats (APTs). Our solution uses advanced threat intelligence, analytics, and automation to detect, investigate, and neutralize threats across endpoints, identities, email, and cloud workloads before they cause damage. With continuous proactive monitoring, real-time alerts, and rapid incident response, we help reduce attack surfaces and minimize risk. Our expert-driven approach ensures your systems, applications, and sensitive data remain secure, resilient, and protected against evolving cybersecurity threats.


























