DMARC Quarantine vs Reject: How to Avoid Losing Legitimate Emails
Email remains one of the most trusted channels for business communication, yet it is also one of the most abused. In my experience working with organizations across industries, email authentication issues often surface only after customers report missing invoices or password reset messages. That is usually when DMARC becomes part of the conversation.
One of the most common questions I hear is about DMARC quarantine vs reject. Both options protect your domain from spoofing and phishing attacks, but choosing the wrong policy too early can block legitimate emails. Understanding how each works is essential if you want strong protection without damaging deliverability.
If you are already focusing on strengthening your Email Security services, DMARC should be a critical part of that strategy.
Understanding DMARC and Why It Matters
DMARC stands for Domain based Message Authentication Reporting and Conformance. It works alongside SPF and DKIM to tell receiving mail servers how to handle emails that fail authentication.
In practical terms, DMARC helps you:
- Prevent domain spoofing
- Gain visibility into all sending sources
- Enforce authentication policies
For organizations investing in broader Data Security solutions, proper email authentication plays a major role in preventing data leakage and impersonation based attacks.
The policy you choose determines how strict your protection will be.
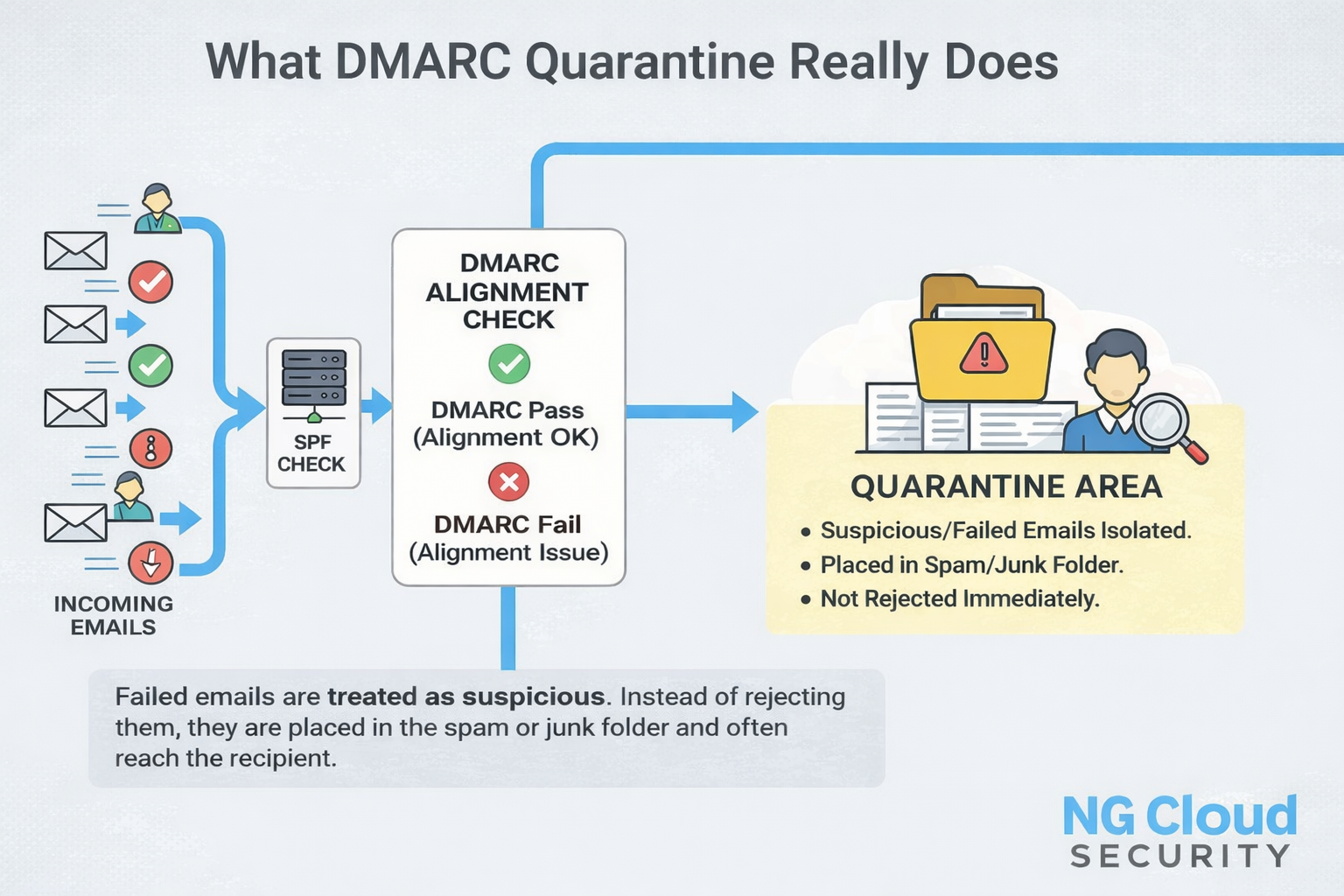
What DMARC Quarantine Really Does
When you set DMARC to quarantine, receiving servers treat failed messages as suspicious. Instead of rejecting them outright, these emails are typically delivered to the spam folder.
From a security operations perspective, quarantine acts as a transitional control. Legitimate emails that fail due to configuration issues may still reach the recipient, though not always in the primary inbox.
Organizations running Microsoft environments should also align DMARC with proper Microsoft 365 Security Assessment to ensure SPF and DKIM are configured correctly.
When Quarantine Makes Sense
Quarantine is ideal during the early stages of implementation. It allows monitoring without completely blocking traffic.
This is especially important if you are using multiple cloud services or marketing platforms. Many companies discover unknown sending sources during this phase. If you operate in a hybrid setup, aligning DMARC with Modern Identity and Access Management ensures authentication alignment across systems.
Risk of Staying on Quarantine Too Long
While quarantine reduces exposure, it does not fully stop spoofing. Malicious emails may still appear in spam folders. Over time, this can impact brand trust and sender reputation.
What DMARC Reject Actually Does
Reject is the strictest policy. It instructs receiving servers to completely block emails that fail authentication. These emails never reach the recipient mailbox.
For organizations operating under Zero Trust principles, reject aligns strongly with enforcement strategies. If your security roadmap already includes Zero Trust Security Services, moving to reject is often the logical final step.
When Reject Is the Right Choice
Reject works best when:
- All legitimate senders pass SPF and DKIM
- DMARC reports show consistent alignment
- Third party services are fully validated
Businesses that rely heavily on Microsoft ecosystems should also ensure alignment with Exchange Online security configuration before enforcing reject.
The Risk of Reject Without Preparation
The biggest risk is silent business disruption. If a billing system, CRM, or HR tool is misconfigured, its emails will be blocked entirely.
I have seen cases where password reset links stopped working simply because DMARC was enforced without reviewing reports properly. That is why a structured security review process, similar to a Cloud Security Assessment, should always precede strict enforcement.
DMARC Quarantine vs Reject: Core Differences
The main difference between DMARC quarantine vs reject lies in enforcement level.
| Comparison Area | DMARC Quarantine | DMARC Reject |
| Enforcement Level | Moderate enforcement | Strict enforcement |
| Failed Email Handling | Delivered to spam or junk folder | Completely blocked by receiving server |
| Delivery Possibility | May still reach recipient in spam | No delivery at all |
| Implementation Stage | Best for monitoring and transition phase | Best after full authentication validation |
| Risk Level | Lower risk of losing legitimate emails | Higher risk if configuration is incomplete |
| Security Strength | Partial protection against spoofing | Strong protection against spoofing |
| Strategy Approach | Observation and gradual enforcement | Full protection and confidence based enforcement |
Both policies are valuable, but timing determines success.
How to Avoid Losing Legitimate Emails
Avoiding legitimate email loss requires a structured approach.
Start With Monitoring Mode
Begin with DMARC policy set to none. This provides reporting visibility without impacting delivery. Analyze reports carefully to identify all email sources.
Authenticate Every Sender
Ensure SPF includes all approved sending services. Configure DKIM properly. Align domains correctly.
If your organization lacks internal expertise, managed services such as Microsoft 365 Managed Services can help maintain authentication consistency.
Transition Gradually
Move from none to quarantine first. Monitor impact. Once reports show stable alignment and no legitimate failures, then move to reject.
Review Reports Continuously
Email infrastructure evolves. New SaaS tools get introduced. Regular monitoring ensures your DMARC policy remains effective and does not disrupt business operations.
Final Thoughts
DMARC is not just a DNS setting. It is a strategic control that protects brand reputation and customer trust.
The decision between DMARC quarantine vs reject should depend on your visibility, risk tolerance, and technical readiness. In my experience, organizations that take a phased and data driven approach avoid unnecessary email loss while achieving strong protection.
When implemented correctly, DMARC strengthens your email security posture, aligns with Zero Trust strategy, and ensures legitimate communication flows without interruption.