Difference Between EDR and Antivirus: Which Offers Better Protection?
The difference between edr and antivirus is one of the most common questions I hear from business owners and IT leaders. Many organizations still depend on traditional antivirus because it feels familiar and safe. Yet the threat landscape has changed faster than most security tools. Attackers no longer behave like the viruses of the past. They think like businesses, use automation, and target weaknesses in people and processes. From my experience advising companies across regions, relying only on antivirus today is similar to locking the main door while leaving every window open.
Endpoint protection must match the reality of modern work. Employees connect from home, data lives in the cloud, and devices move across networks. To understand what truly protects a business, we need to explore how antivirus and EDR work, where each one fits, and why the gap between them keeps growing.
What Traditional Antivirus Actually Does
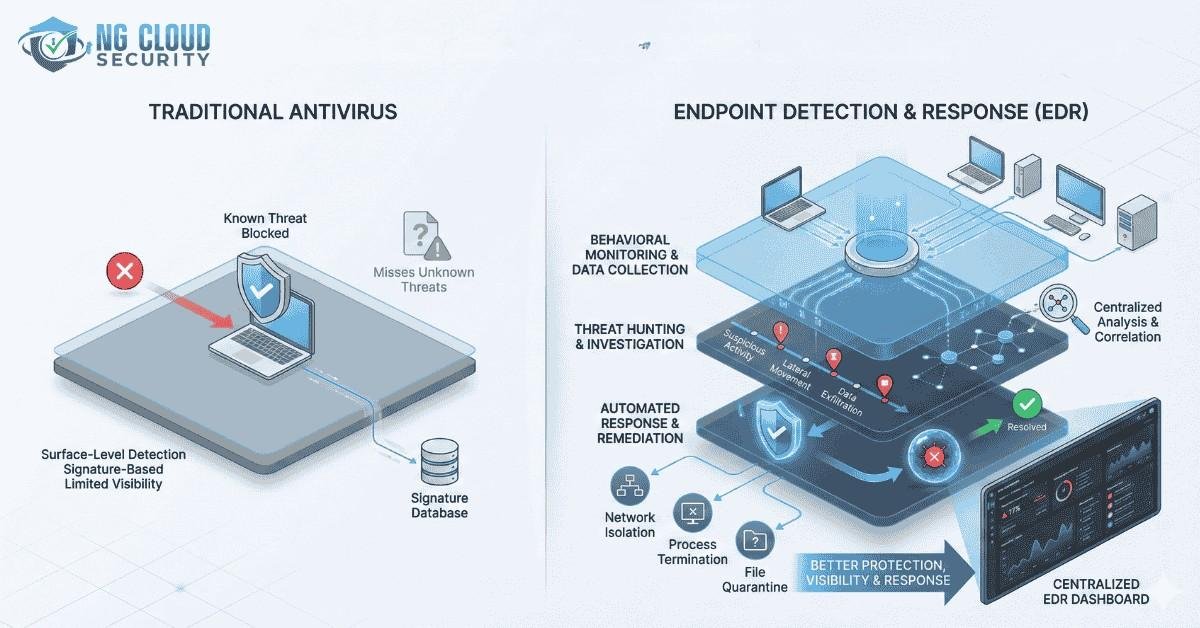
Antivirus was built for a simpler digital world. Its main job is to compare files on a computer with a database of known malicious signatures. When the software finds a match, it blocks or removes the file. Over the years, vendors added scheduled scans, email attachment checks, and basic web filtering. For everyday nuisance malware, this approach still stops many threats.
In small environments antivirus can reduce noise and prevent accidental downloads. It also offers automatic updates and requires little skill to manage. These strengths made antivirus the default choice for decades. However, the method depends on yesterday knowledge. If an attack looks new or behaves differently, antivirus often stays silent.
Where Antivirus Struggles
The core weakness is visibility. Antivirus focuses on files, not on actions. Modern intrusions rarely begin with an obvious malicious file. Attackers use built in administration tools, stolen credentials, and cloud services that appear legitimate. None of this matches a classic signature.
During several investigations I led, antivirus dashboards showed perfect health while unauthorized access was active for weeks. The tool could not explain who logged in, what commands were executed, or how data moved outside the network. Without that context, security teams remain blind.
What Endpoint Detection and Response Brings
EDR changes the perspective completely. Instead of asking only whether a file is bad, EDR records everything happening on the device. It watches processes, network connections, user behavior, and system changes. Analytics then look for patterns that resemble an attack.
This approach is at the heart of modern endpoint security services offered today. With EDR, analysts receive a clear timeline of events. They can see how an email led to a script, how the script tried to contact an external server, and which other machines were touched. The technology supports remote containment, forensic collection, and guided investigation.
Real Difference Between EDR and Antivirus
The difference between edr and antivirus appears in three major areas: detection, visibility, and response.

Detection:
Antivirus depends on signatures of known malware. EDR depends on behavior and anomalies. Even if no malicious file exists, EDR can recognize suspicious activity.
Visibility:
Antivirus provides simple alerts for one device. EDR correlates data from many endpoints and reveals the full story of an incident.
Response:
Antivirus usually deletes a file and stops. EDR can isolate a machine, stop a process, roll back changes, and allow experts to investigate remotely. Solutions such as Defender for XDR by NG Cloud Security build on this capability to protect organizations at scale.
How Modern Attacks Evade Antivirus
Criminal groups now operate like professional enterprises. They buy access from brokers, test defenses, and customize techniques for each target. Many attacks live only in memory and never touch the disk. Others misuse remote management features or cloud identities.
Antivirus sees these actions as normal because no signature matches. EDR sees the unusual sequence of behavior. That is why an endpoint security assessment becomes essential before deciding the right control. Assessment reveals gaps that traditional tools hide.
Practical Use Cases for Antivirus
Despite its limits, antivirus still has a role. It blocks common ransomware families, scans USB devices, and filters known dangerous downloads. For personal laptops or very small offices, antivirus may serve as a basic safety layer. It also helps organizations meet minimal compliance expectations.
Yet antivirus should be viewed as hygiene, not as a strategy. Businesses handling customer data, financial information, or intellectual property need deeper protection than signatures alone.
Practical Use Cases for EDR
EDR proves its value in complex environments. Remote work, cloud applications, and multi location operations create blind spots that only continuous monitoring can cover. EDR supports threat hunting, insider risk detection, and rapid containment during incidents.
Teams using SOC managed services often rely on EDR as the primary sensor. Analysts can investigate alerts without visiting the site and respond within minutes. This speed makes the difference between a minor event and a major breach.
Compliance and Governance Perspective
Regulators increasingly expect organizations to demonstrate detection and response capability. Simple antivirus logs rarely satisfy auditors. EDR provides detailed evidence of what happened and how the company reacted. Frameworks aligned with Zero Trust security services emphasize monitoring every action rather than trusting devices by default.
Operational Reality Inside Companies
Technology alone does not create security. Antivirus requires little attention, while EDR demands process and skills. Alerts must be reviewed, playbooks defined, and responsibilities assigned. Without guidance, teams may feel overwhelmed by data.
This is where managed operations become important. Services such as managed IT and security operations combine EDR tools with human expertise. From my experience, organizations gain the most value when technology and people work together rather than treating software as a magic box.
Can Both Work Together
Yes, antivirus and EDR can complement each other. Antivirus handles commodity malware with minimal effort. EDR focuses on advanced behavior and investigation. Many deployments keep a lightweight antivirus while EDR acts as the central brain. The key is integration and clear ownership of alerts.
How EDR Relates to Broader Security
EDR often connects with platforms like Microsoft Defender for XDR, identity monitoring, and cloud analytics. These integrations create a wider picture across email, applications, and networks. Antivirus alone cannot provide this ecosystem view.
Business Impact of Choosing Wrong
When leaders evaluate only license cost, antivirus appears cheaper. The real calculation must include downtime, data loss, and reputation damage. One ransomware incident can cost more than several years of EDR investment. I have seen companies pause operations for days because early signals were missed.
Steps to Select the Right Approach
- Identify critical assets and sensitive data.
- Review current visibility gaps.
- Conduct an independent endpoint security assessment.
- Define response objectives and acceptable downtime.
- Train teams or engage managed experts.
Implementation Lessons from Experience
Start with a pilot group and clear success criteria. Tune policies to reduce false alerts. Document response procedures before a crisis occurs. Regularly test isolation and recovery features. Security improves through practice, not through installation alone.
Future Direction of Endpoint Protection
Artificial intelligence now supports both antivirus and EDR, yet behavior monitoring remains the decisive factor. Attackers also use automation, so defenses must learn continuously. The trend points toward platforms that combine endpoint data with identity and cloud signals, an approach embodied in modern XDR strategies.
Making the Decision
For organizations with remote staff, cloud workloads, or valuable information, EDR should be the foundation. Antivirus can remain as an assistant, but not as the main guardian. The difference between edr and antivirus ultimately reflects the difference between looking at a single file and understanding the entire story of an attack.
Closing Reflection
Endpoint security shapes business resilience. Based on years of guiding digital transformation, I have learned that visibility beats assumptions. Antivirus brought protection to the early internet era, while EDR addresses the realities of today. Companies that adopt behavior driven defense gain confidence to innovate without fear.
Choosing wisely is not about following trends. It is about protecting people, data, and trust. When leaders understand the true difference between edr and antivirus, they can invest in controls that support growth rather than simply reacting to threats.