Microsoft 365 Defenders
Protecting Your Business from Cyber Threats.
As businesses increasingly rely on Microsoft 365 (M365) for their day-to-day operations, the need for effective cybersecurity measures becomes more critical than ever. At NG Cloud Security, we offer M365 Defenders as a comprehensive cybersecurity solution to help protect your business from cyber threats.
M365 Defenders is a suite of security services that are designed to provide real-time protection against a range of threats, including malware, phishing, and ransomware attacks. Our team of cybersecurity experts can help you implement M365 Defenders to ensure that your business is protected from the latest threats.
With M365 Defenders, you can enjoy peace of mind knowing that your business is secure. Our solution is designed to work seamlessly with M365, providing a comprehensive security platform that can help you identify and respond to potential threats quickly.
M365 Defenders provides a wide range of security services, including:
- Advanced Threat Protection: Protects against known and unknown malware, phishing, and other cyber threats.
- Identity and Access Management: Helps manage access to your organization’s resources and information.
- Security Management: Provides insights and reports on the security of your M365 environment, allowing you to take proactive measures to improve your security posture.
At NG Cloud Security, we understand that every business has unique cybersecurity needs. That’s why we work closely with our clients to develop customized security solutions that are tailored to their specific requirements.
Here’s a list of the different Microsoft 365 Defender products and solutions that Microsoft 365 Defender coordinates with:
- Microsoft Defender for Endpoint.
- Microsoft Defender for Office 365.
- Microsoft Defender for Identity.
- Microsoft Defender for Cloud Apps.
- Microsoft Defender Vulnerability Management.
- Azure Active Directory Identity Protection.
- Microsoft Data Loss Prevention.
- App Governance.
If you’re looking for a reliable cybersecurity solution for your business, look no further than M365 Defenders. Contact us today to learn more about how we can help you protect your business from cyber threats.
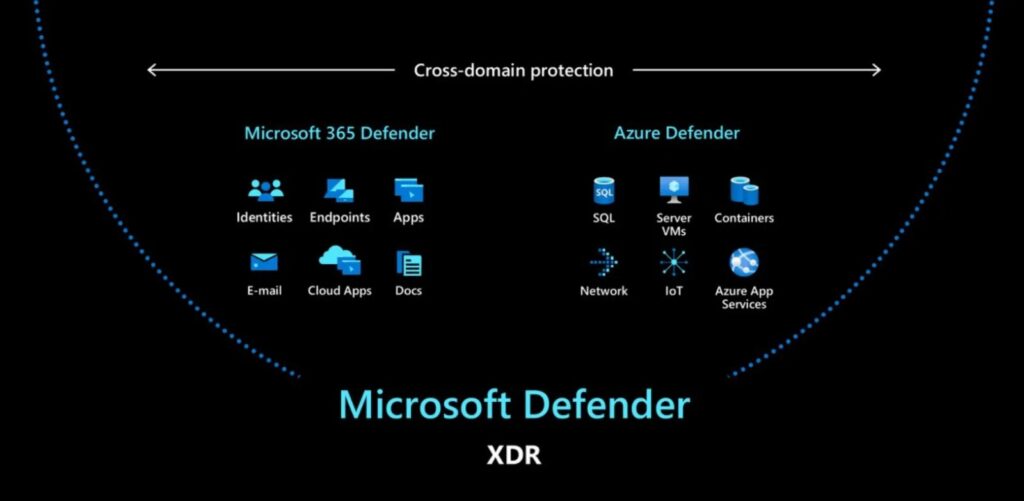
Microsoft Sentinel
Your Comprehensive Security Information and Event Management Solution.
MS Sentinel is a cloud-native security information and event management (SIEM) solution offered by NG Cloud Security. It provides a comprehensive view of the security of your entire organization by collecting, analyzing, and correlating data from various sources across your infrastructure, including on-premises systems and cloud services.
With MS Sentinel, your organization can detect and respond to threats in real-time, minimizing the impact of security incidents. It provides intelligent security analytics and threat intelligence, as well as automation and orchestration capabilities to help you respond to threats quickly and efficiently.
At NG Cloud Security, we specialize in MS Sentinel deployment and management. Our team of cybersecurity experts can help you implement MS Sentinel, configure it to meet your specific needs, and provide ongoing support and maintenance.
With our MS Sentinel services, you can:
- Gain real-time visibility into your organization’s security posture.
- Detect and respond to threats quickly and efficiently.
- Reduce the risk of data breaches and other security incidents.
- Automate and streamline your security operations.
- Ensure compliance with regulatory requirements.
Protect your organization from advanced cyber threats with NG Cloud Security’s MS Sentinel services. Contact us today to learn how we can help you implement and manage MS Sentinel.

Endpoint Security
Endpoint Security is a critical aspect of any organization’s cybersecurity strategy. With the increasing sophistication of cyber attacks, it’s more important than ever to protect your endpoints, including laptops, desktops, and mobile devices. At NG Cloud Security, we offer Endpoint Security as a comprehensive service to help safeguard your organization’s endpoints.
Our Endpoint Security solution is designed to provide complete protection against a range of cyber threats, including malware, ransomware, phishing, and other attacks. We use advanced technologies such as next-generation antivirus, firewall, and intrusion prevention systems to detect and prevent threats before they can cause any harm to your organization.
Our team of cybersecurity experts works with you to design and implement an Endpoint Security strategy that meets your organization’s specific needs. We conduct a thorough assessment of your current security posture, identify vulnerabilities and risks, and develop a customized plan to strengthen your defenses.
Our Endpoint Security service also includes 24/7 monitoring and support to ensure that your endpoints are always protected. We use advanced threat intelligence and analytics to detect and respond to threats in real-time, and our team of experts is always on hand to provide assistance and guidance.
In addition to providing robust protection, our Endpoint Security service also helps you achieve compliance with industry regulations and standards such as HIPAA, PCI DSS, and GDPR.
With NG Cloud Security’s Endpoint Security service, you can rest assured that your organization’s endpoints are in safe hands. Contact us today to learn more about how we can help you protect your endpoints and safeguard your organization from cyber threats.

Windows Hello for Business + Passwordless
Windows Hello for Business + Passwordless is a powerful cybersecurity solution that provides multi-factor authentication for Windows devices. This innovative security solution offers a password-free experience for users, while maintaining the highest levels of security for your business.
At NG Cloud Security, we offer Windows Hello for Business + Passwordless as part of our comprehensive cybersecurity services. Our team of experts can help you implement this powerful solution, giving your business the protection it needs against the latest cyber threats.
With Windows Hello for Business + Passwordless, you can eliminate the need for passwords, reducing the risk of phishing attacks and password-related security breaches. This solution uses biometric authentication, such as facial recognition or fingerprint scanning, to ensure that only authorized users can access your business data.
Our team can work with you to configure and customize Windows Hello for Business + Passwordless to meet your specific business needs. We can also provide ongoing support and training to ensure that you and your team are comfortable using this cutting-edge security solution.
If you’re looking for a powerful and innovative way to protect your business from cyber threats, Windows Hello for Business + Passwordless is the solution for you. Contact us today to learn how we can help you implement this solution and strengthen your cybersecurity defenses.

Conditional Access Policy
Securely accessing corporate resources from anywhere, at any time, on any device is essential for modern businesses. However, this increased accessibility can also increase the risk of security threats.
At NG Cloud Security, we provide Conditional Access Policy as part of our comprehensive cybersecurity services to help protect your organization from unauthorized access while enabling your team to work seamlessly.
Our Conditional Access Policy service allows you to set specific rules that determine who, what, where, and how users can access your corporate resources. This way, you can easily manage and control access to your applications, data, and other sensitive information.
With our Conditional Access Policy service, you can set rules based on a range of conditions such as the user’s location, device, application, and risk level. For example, you can create a rule that requires multi-factor authentication for users accessing corporate data from outside the office.
Our team of experts can help you implement and customize Conditional Access Policies to fit your unique business needs. We will work with you to understand your security requirements and tailor the policies accordingly.
By utilizing our Conditional Access Policy service, you can reduce the risk of data breaches and unauthorized access, increase compliance, and enhance your organization’s overall security posture.
Contact us today to learn more about our Conditional Access Policy service and how we can help you protect your organization from cyber threats.
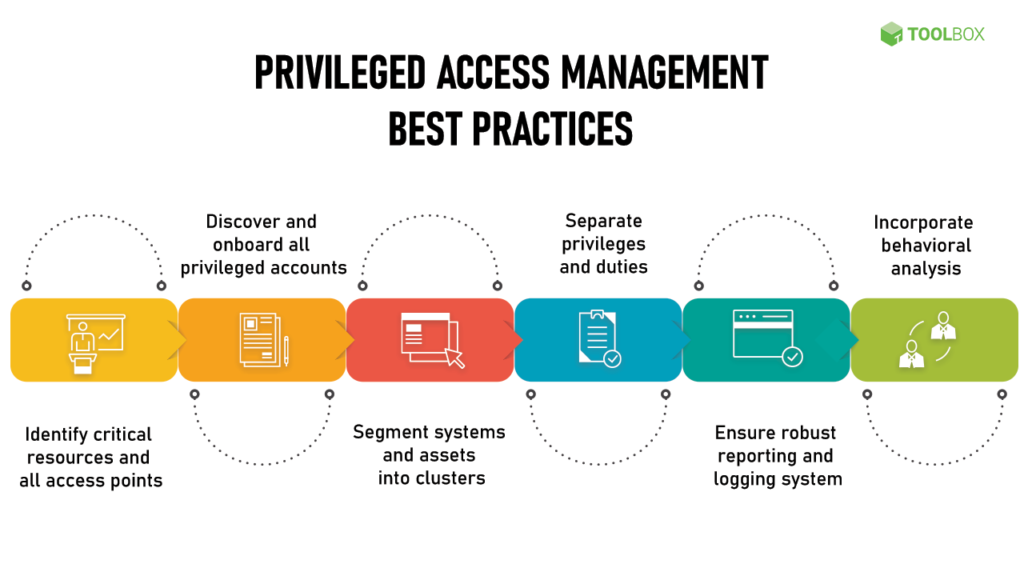
Privilege Access Management
Protecting your organization’s critical data and assets requires a comprehensive approach to cybersecurity. One important aspect of this approach is managing privileged access. NG Cloud Security offers a powerful Privilege Access Management (PAM) service to help your organization mitigate the risks of privileged accounts and access.
With our PAM service, you can manage, monitor, and control access to critical systems and data from a central location. Our solution provides granular access controls and monitoring capabilities, ensuring that only authorized users have access to sensitive information.
Our PAM service provides a number of key features, including:
- Access Request and Approval: Requests for privileged access are automatically routed to authorized approvers, ensuring that access is granted only to those with a legitimate business need.
- Just-in-Time Access: Privileged access is granted on a temporary basis, reducing the risk of unauthorized access and preventing attackers from gaining a foothold in your environment.
- Session Recording and Monitoring: All privileged sessions are recorded and monitored in real-time, providing a comprehensive audit trail for compliance and security purposes.
- Role-Based Access Control: Our solution allows you to define roles and policies to ensure that access is granted on a need-to-know basis, minimizing the risk of insider threats.
Our PAM service integrates seamlessly with your existing infrastructure, enabling you to manage privileged access across your entire environment from a single pane of glass. With NG Cloud Security, you can ensure that your organization’s critical assets are protected against unauthorized access, helping you stay ahead of today’s constantly evolving threat landscape.
Contact us today to learn more about how our PAM service can help your organization protect against privileged access threats.

Privilege Identity Management
Protect Your Business with Privileged Identity Management from NG Cloud Security
Privileged accounts, such as those of administrators, have access to critical business systems and data. They are also attractive targets for cybercriminals. Without proper management and protection, these accounts can become a significant security risk.
At NG Cloud Security, we understand the importance of protecting privileged identities. That’s why we offer Privileged Identity Management as one of our core cybersecurity services.
Our Privileged Identity Management service provides a comprehensive solution for managing and securing privileged accounts. We help you identify all privileged accounts in your organization, monitor their activities, and control their access to sensitive data and systems.
With our Privileged Identity Management service, you can:
- Discover all privileged accounts across your IT environment.
- Implement least-privileged access controls and enforce password policies.
- Monitor all privileged account activities and alerts for any suspicious behavior.
- Control access to privileged accounts and enable multi-factor authentication.
- Provide just-in-time access to privileged accounts for specific tasks.
Our team of cybersecurity experts will work closely with you to implement the best practices and policies to secure your privileged accounts. We also provide regular reporting and insights into your privileged account activities, so you can continuously improve your security posture.
Protect your business from cyber threats by securing your privileged accounts with NG Cloud Security’s Privileged Identity Management service. Contact us today to learn more.
Multi-Factor Authentication
MFA (Multi-Factor Authentication) is a critical component of any security strategy. It provides an additional layer of protection for your sensitive information by requiring multiple forms of authentication before granting access. At NG Cloud Security, we offer MFA as a service to help businesses of all sizes protect their valuable data from unauthorized access.
With MFA, users are required to provide two or more forms of authentication before accessing their accounts. This can include something they know (such as a password), something they have (such as a mobile device), or something they are (such as biometric data). By requiring multiple forms of authentication, MFA significantly reduces the risk of unauthorized access, even if an attacker has obtained a user’s password.
NG Cloud Security offers MFA as a cloud-based service, which means there’s no need to install additional hardware or software on your premises. Our team of security experts will work with you to configure and deploy MFA across your organization, ensuring that all users are protected and that the implementation is seamless and hassle-free.
Our MFA solution is easy to use, with a simple and intuitive interface that makes it easy for your users to authenticate themselves. It’s also highly customizable, allowing you to configure policies and settings to meet your specific security requirements.
NG Cloud Security’s MFA service provides a wide range of benefits, including:
- Enhanced security: MFA provides an additional layer of security that significantly reduces the risk of unauthorized access.
- Easy implementation: Our cloud-based solution is easy to implement, with no additional hardware or software required.
- Customizable policies: Our MFA solution is highly customizable, allowing you to configure policies and settings to meet your specific security requirements.
- Seamless user experience: Our MFA solution is designed to provide a seamless user experience, with a simple and intuitive interface that makes it easy for users to authenticate themselves.
- Compliance: MFA is a critical component of many compliance frameworks, including GDPR, HIPAA, and PCI DSS.
At NG Cloud Security, we take security seriously, and we understand that MFA is an essential tool for protecting your business from cyber threats. Contact us today to learn more about our MFA service and how we can help you protect your valuable data from unauthorized access.

Center for Internet Security
CIS (Center for Internet Security) Benchmarks are industry-standard best practices for securing systems and applications against cyber threats. Implementing CIS Benchmark policies can help organizations meet compliance requirements, reduce risk exposure, and improve overall security posture.
NG Cloud Security provides CIS Benchmark Policy as a service to help organizations efficiently implement and manage CIS Benchmark policies in their IT environment. Our service includes the following features:
CIS Benchmark Policies: We provide pre-built, ready-to-use CIS Benchmark policies for various platforms, including Windows, Linux, and Cloud services. These policies are regularly updated to reflect the latest CIS Benchmark standards and security best practices.
Policy Automation: We use automation tools to apply CIS Benchmark policies to IT assets and enforce policy compliance. This reduces manual effort and ensures consistency across the environment.
Policy Management: We provide a centralized policy management console to view and manage policy settings, exceptions, and reporting. This helps organizations quickly identify and remediate compliance issues.
Compliance Reporting: We provide compliance reporting that shows how well the organization is adhering to CIS Benchmark policies. Our reports provide a detailed overview of policy status, exceptions, and recommended remediation steps.
With NG Cloud Security’s CIS Benchmark Policy service, organizations can ensure their IT environment is secure and compliant with industry-standard best practices. Contact us today to learn more about how we can help you implement CIS Benchmark policies in your organization.

Azure Cloud Security
Azure Cloud Security by NG Cloud Security
Securing your cloud environment is crucial in ensuring the safety and privacy of your organization’s data. At NG Cloud Security, we understand the importance of cloud security and provide comprehensive Azure Cloud Security services to protect your cloud workloads from threats.
Our Azure Cloud Security solution includes various security features, such as:
- Azure Security Center: Gain visibility into your cloud environment and detect and respond to threats with Azure Security Center. Our team will help you configure and manage Security Center to identify and remediate potential security risks.
- Azure Network Security: Secure your Azure network infrastructure with NG Cloud Security’s Azure Network Security solutions. We will help you implement network security groups, virtual private networks (VPNs), and other security measures to protect your Azure network from unauthorized access.
- Azure Identity and Access Management (IAM): Control who has access to your cloud resources with Azure IAM. Our team will help you define and enforce access policies, manage identities and access, and provide identity protection for your Azure environment.
- Azure Encryption: Protect your data at rest and in transit with Azure Encryption. We will help you implement encryption solutions for your Azure data, including storage encryption, database encryption, and SSL/TLS encryption.
- Azure Compliance and Governance: Meet regulatory requirements and achieve compliance with Azure Compliance and Governance. Our team will help you implement compliance policies and monitor your cloud environment for compliance violations.
At NG Cloud Security, we take a comprehensive approach to Azure Cloud Security, providing end-to-end security solutions that address all aspects of your cloud environment. Contact us today to learn more about our Azure Cloud Security services and how we can help you secure your cloud workloads.

Active Directory Security
Active Directory (AD) is a crucial component of any organization’s IT infrastructure, as it provides a centralized database for managing user accounts, authentication, and authorization. However, because AD is so critical, it is often targeted by cyber attackers looking to gain access to an organization’s sensitive information.
At NG Cloud Security, we understand the importance of securing AD, and we offer a range of services to help our clients protect this critical component of their infrastructure. Our AD security services are designed to help our clients improve the security of their AD environments, reduce their exposure to cyber threats, and ensure compliance with industry regulations and standards.
Our AD security services include:
- AD Security Assessment: Our team of security experts will perform a comprehensive assessment of your AD environment to identify vulnerabilities, misconfigurations, and other security risks.
- AD Hardening: We will work with you to implement best practices for securing AD, including configuring Group Policy Objects (GPOs), implementing two-factor authentication (2FA), and deploying security tools such as Microsoft Advanced Threat Analytics (ATA).
- AD Monitoring: Our team will monitor your AD environment 24/7 to detect and respond to any security incidents or anomalies, such as account lockouts, failed login attempts, and unusual activity.
- AD Backup and Recovery: We will implement a backup and recovery strategy for your AD environment, ensuring that you can quickly recover from any data loss or corruption.
- AD Compliance: We will help you ensure compliance with industry regulations and standards such as HIPAA, PCI-DSS, and GDPR by implementing the necessary security controls and processes.
Our AD security services are designed to be flexible and scalable, so we can tailor our services to meet the specific needs of your organization. We work closely with our clients to ensure that they have a comprehensive understanding of the security risks facing their AD environment and the steps they can take to mitigate those risks.
If you are interested in learning more about our AD security services, please contact us today to schedule a consultation with one of our security experts.

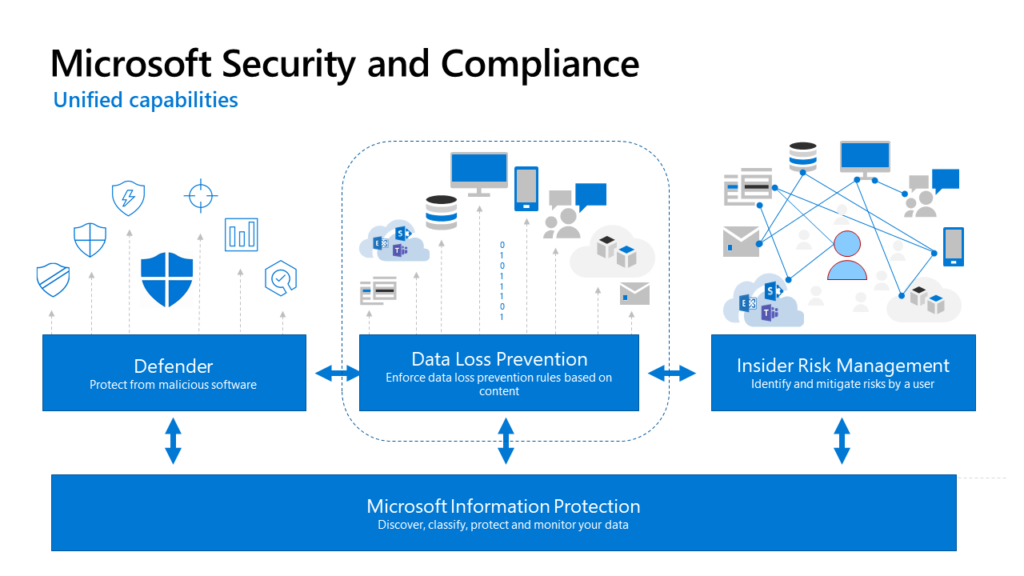
Email Security (M Information Protection+DLP)
Email communication is an essential part of business operations, but it also poses significant cybersecurity risks. The increasing number of cyberattacks targeting emails, such as phishing, ransomware, and business email compromise (BEC), highlights the importance of implementing robust email security solutions.
NG Cloud Security’s Email Security service, powered by Microsoft Information Protection (MIP) and Data Loss Prevention (DLP), provides comprehensive protection for your organization’s emails. MIP and DLP use machine learning algorithms to identify and protect sensitive information, such as financial data, intellectual property, and personal information, from being accidentally or maliciously disclosed.
Key Features:
- Prevent data loss: NG Cloud Security’s Email Security service uses MIP and DLP to identify sensitive information in your organization’s emails and prevent it from being leaked or shared without proper authorization.
- Anti-phishing: Our email security solution detects and blocks phishing attempts, preventing employees from falling prey to malicious links or attachments.
- Ransomware protection: Our email security solution is equipped with advanced ransomware protection capabilities that can identify and stop ransomware attacks before they can cause damage to your organization’s systems.
- Customizable policies: Our email security solution allows you to create customized policies that reflect your organization’s unique security requirements.
NG Cloud Security’s Email Security service is easy to deploy, and it integrates seamlessly with Microsoft 365, providing a centralized location to manage email security policies across your organization. Our team of cybersecurity experts is available 24/7 to provide support and monitor your organization’s email security.
Contact us to learn more about our Email Security (MS Information Protection + DLP) service and how it can help protect your organization’s sensitive information.
Security Assessment
Protecting your organization from cyber threats is critical. But how do you know if your security measures are working effectively? NG Cloud Security offers a comprehensive Security Assessment service to help you identify and address potential vulnerabilities.
Our team of experts will conduct a thorough analysis of your organization’s security posture, including:
- Network infrastructure.
- Cloud environment.
- Endpoint security.
- Identity and access management.
- Security policies and procedures.
Using industry-standard tools and techniques, we’ll identify weaknesses and provide recommendations for improving your security posture. Our detailed report will highlight areas of concern and provide a prioritized action plan for addressing them.
We understand that every organization is unique, so we tailor our assessments to meet your specific needs. Whether you’re looking for a high-level overview or a deep dive into your security controls, we can help.
Don’t wait until it’s too late. Contact NG Cloud Security today to schedule your Security Assessment and protect your organization from cyber threats.