- What is Microsoft LAPS?
You can easily change the password of your domain administrator account, but what about the local administrator account? The password of the local admin account is often set during installation, but you can’t easily change it on all computers. This is where Windows LAPS comes in. LAPS stands for Local Administrator Password Solution.
With LAPS we can automatically set unique local administrator passwords on each computer, which are stored in the Azure Active Directory or in your local Active Directory. The password is automatically changed every 30 days by default.
There are more advantages:
- Store password in Azure AD – Easier to retrieve password
- Password History – View previous passwords, useful for recovery scenarios
- Encrypt passwords – Improves security in local Active Directory
- Automatically rotate password – Reset password after the account is used
- View with Microsoft Graph – You can retrieve the passwords with Microsoft Graph
- DSRM Password Backups – Secure and rotate the domain controller recovery password
- New PowerShell Module – Gives you more control through PowerShell
- Dedicated event log – Makes it easier to troubleshoot issue
Operating system updates
This feature is now available on the following Windows OS platforms with the specified update or later installed:
- Windows 11 22H2 – April 11 2023 Update
- Windows 11 21H2 – April 11 2023 Update
- Windows 10 20H2, 21H2 and 22H2 – April 11 2023 Update
- Windows Server 2022 – April 11 2023 Update
- Windows Server 2019 – April 11 2023 Update
Join Types
LAPS is supported on Microsoft Entra joined or Microsoft Entra hybrid joined devices only. Microsoft Entra registered devices aren’t supported.
License requirements
LAPS is available to all customers with Microsoft Entra ID Free or higher licenses. Other related features like administrative units, custom roles, Conditional Access, and Intune have other licensing requirements.
Enabling Windows LAPS:
Open Microsoft Entra (AAD) > Devices > All Devices > Device settings.
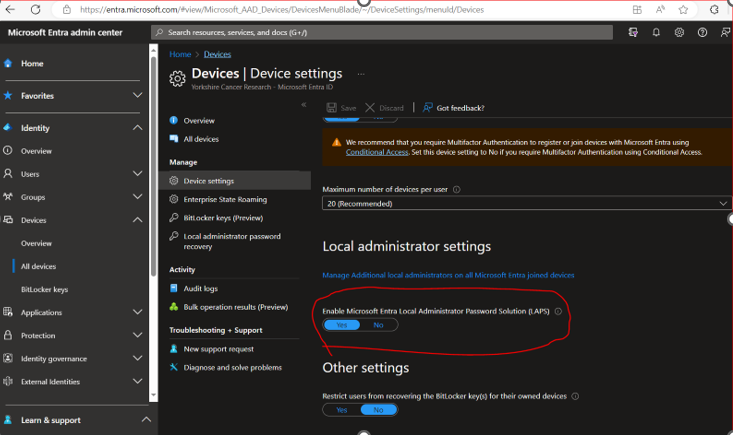
Intune LAPS Setup
Step- 1
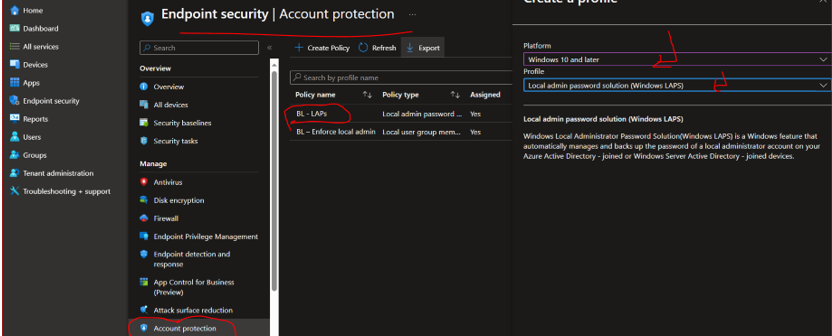
- Intune
- Endpoint Security –> Account Protection
- Create new profile name BL – LAPS,
- profile type: Local admin password solution (LAPS)
- Endpoint Security –> Account Protection
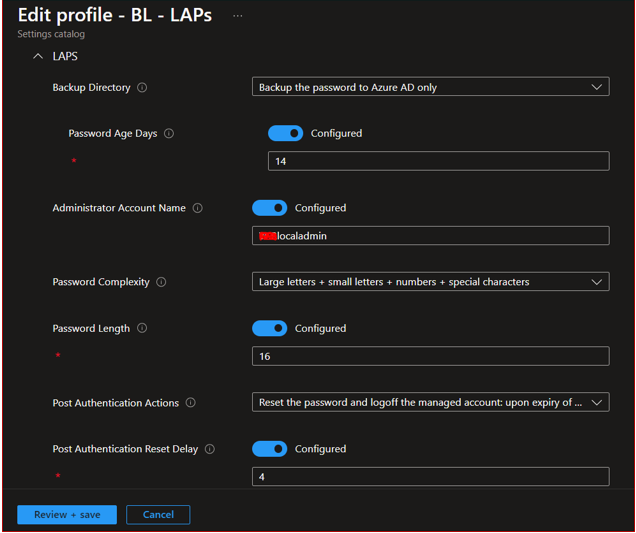
- Backup Directory: Backup the password to Azure AD only
- Password Age Days: 14
- Administrator Account Name: XYZlocaladmin (Name it as per requirements, this would be your Local administrator account(LAPS) on Device)
- Password Complexity: Large letters + small letters + numbers + special characters
- Password Length: 16
- Post Authentication Actions: Reset the password and logoff the managed account: upon expiry of the grace period, the managed account password will be reset and any interactive logon sessions using the managed account will terminated.
- Post Authentication Reset Delay: 4
- Assignment: Intune – Assign your Device group. (Recommend to add Pilot Test group)
- Exclude: Device group if Any
Step- 2
- Create new profile
- Endpoint Security –> Account Protection
- name BL – Enforce local admin accounts, profile type: Local user group membership
- Assignment: Intune – Assign your Device group. (Recommend to add Pilot Test group)
- Exclude: Add Device group if any
- Assignment: Intune – Assign your Device group. (Recommend to add Pilot Test group)
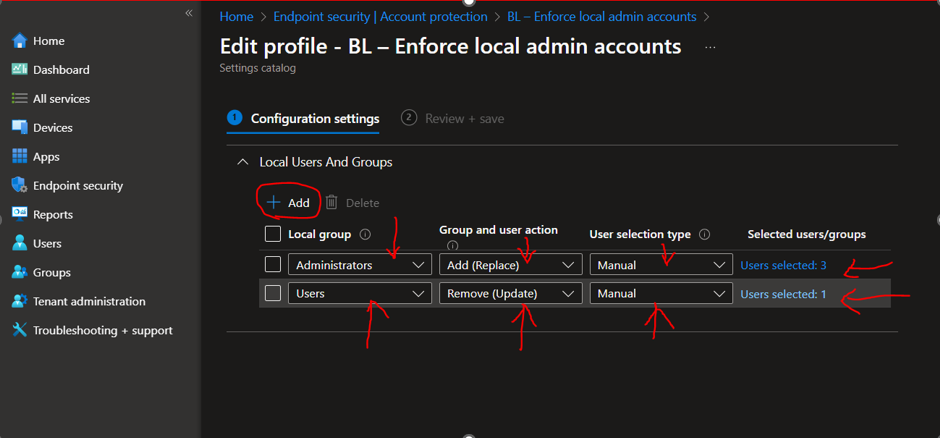
- Add
- Local group: Administrators
- Group and user actions: Add (replace)
- User selection type: Manual
- XYZlocaladmin XYZlocaladmin (Name it as per requirements, this would be your Local administrator (LAPS) account on Device)
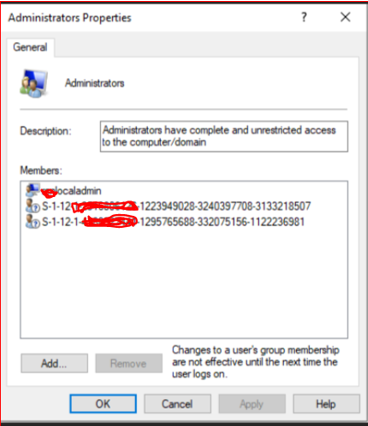
- S-1-12-1-zzzzzzzzzz-yyyyyyyyyy-xxxxxxxxxx-xxxxxxxxx
- S-1-12-1- zzzzzzzzzz-yyyyyyyyyy-xxxxxxxxxx-xxxxxxxxx
- Local group: Administrators
Here you can add
Local Group à Administrator
Group and user action –> Add(replace)
User Selection –> Manual
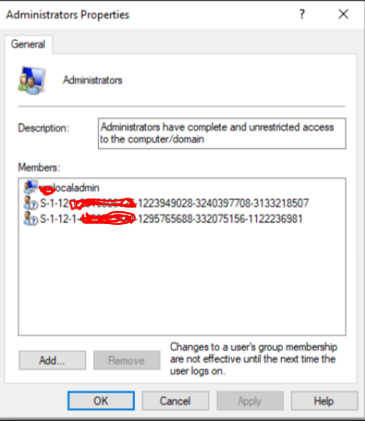
Select users / Groups –> Here you can add your LAPS Local administrator “XYZlocaladmin” and Global Admin SID and local admin SID from Intune enrolled any devices.
SID is unique to each Tenant (You can find SID from any devices that are already enrolled with Intune), This will help to manage the local admins.
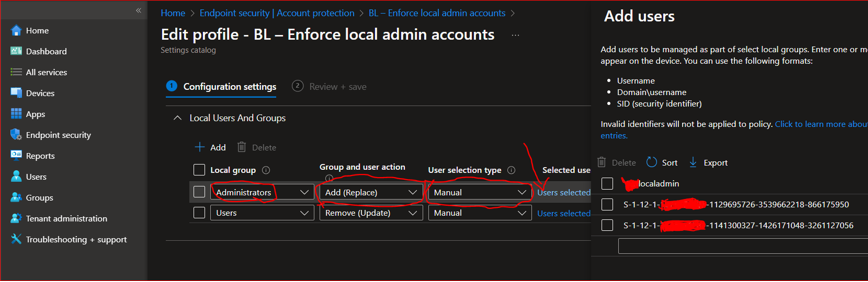
If you already have any local administrator configured for InTune enrolled Devices, you can remove/update by using below settings for your New LAPS
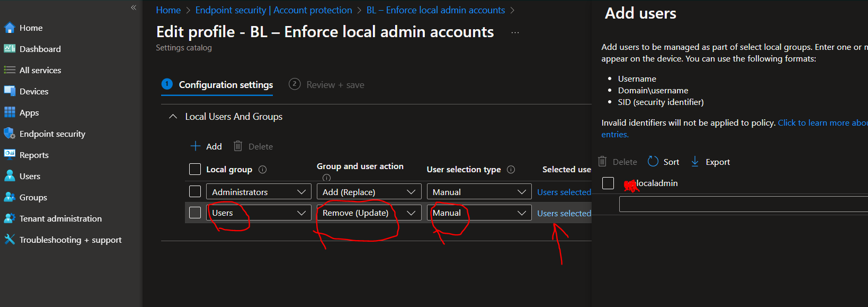
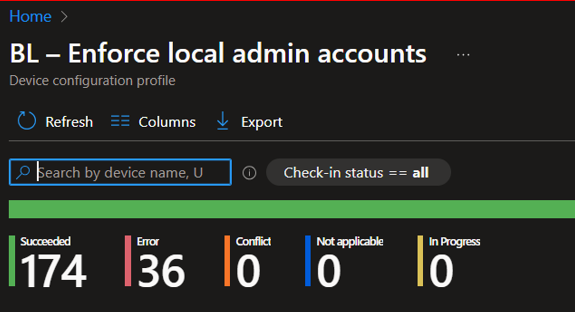
*** give it a few days hopefully Error clears itself
STEP-3
- Create a Configuration profiles (Devices – Configuration Profiles)
-
- Create new profile name BL – Local Administrator, profile type: windows 10 and Later / Setting Catalogue
-
- Administrative Templates\Laps
- Do not allow password expiration time longer than required by policy: Enabled
- Enable local admin password management: Enabled
- Name of administrator account to manage: Enable
- Enter your LAPS administrator account à XYZlocaladmin
- Local Policies Security Options
- Accounts Enable Administrator Account Status: Enabled
- Accounts Rename Administrator Account: XYZlocaladmin (Accounts: Rename administrator account This security setting determines whether a different account name is associated with the security identifier (SID) for the account Administrator. Renaming the well-known Administrator account makes it slightly more difficult for unauthorized persons to guess this privileged user name and password combination. Default: Administrator.)
- Assignment: Intune – Assign your Pilot group / device groups
- Exclude: If any
- Do not allow password expiration time longer than required by policy: Enabled
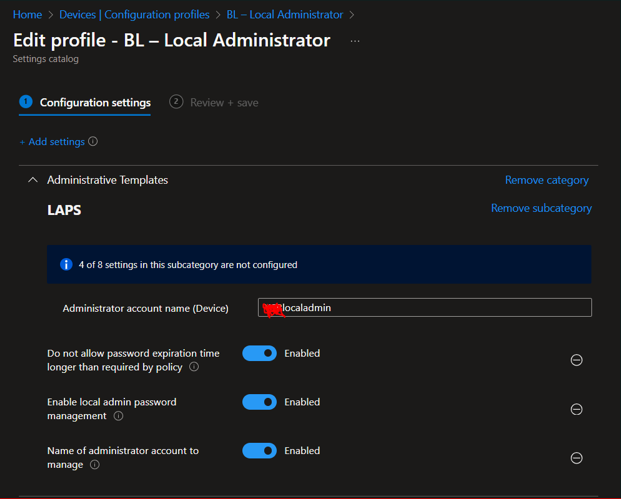
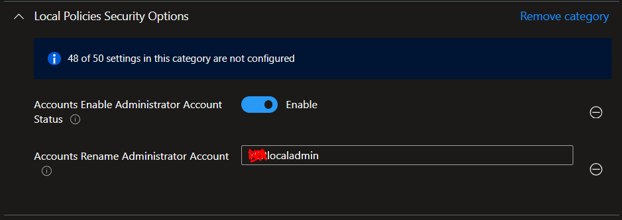
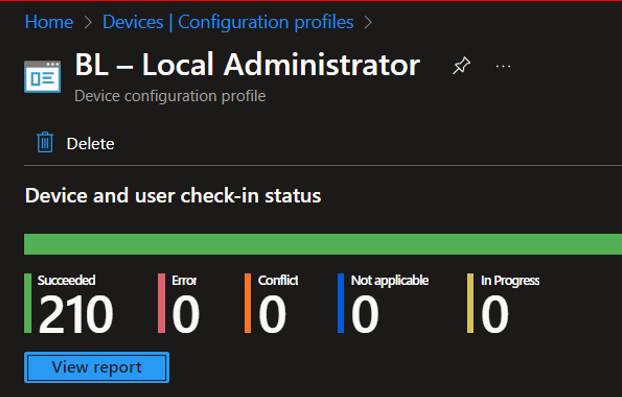
Now your LAPS has been configured , Give it for few hours – syncing and enabling LAPS on assigned Devices.
Now you could see your LAPS has been enabled on your enrolled devices.
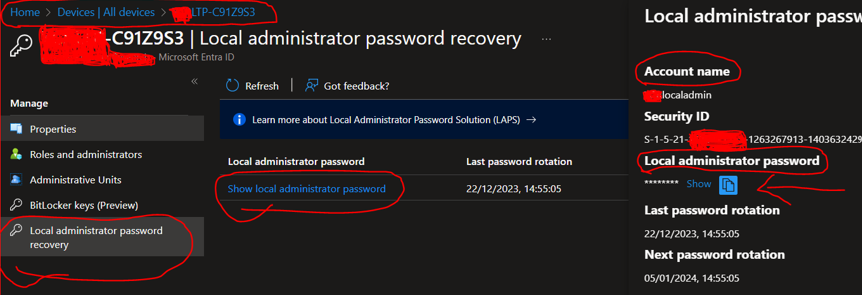
How to Retrieve a device’s local admin password:
Open Microsoft Entra (AAD) > Devices > All devices.—select the device -> Manage -> Local Administrator Password Recovery ->
Show Local administrator Password ->
OR
Endpoint Manager -> Devices -> Windows devices -> select the device à Local Admin Password à Show Local Administrator
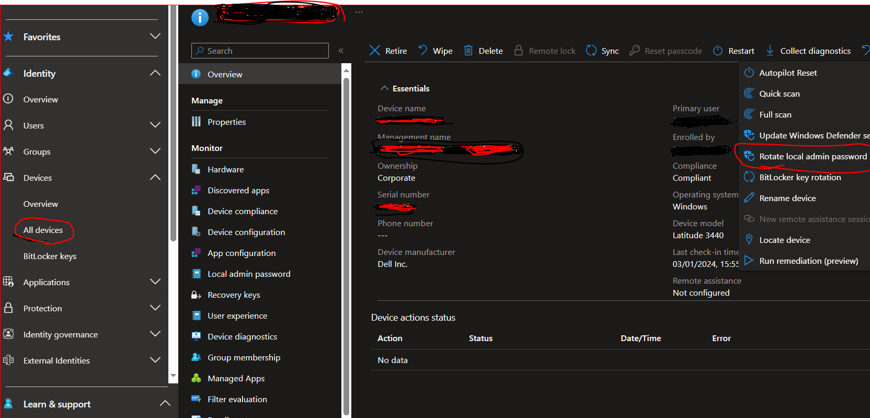
How to manually Rotate a device’s local admin password:
- Open Microsoft Entra (AAD) > Devices > All devices.—select the device -> Manage ->
- On the top bar of quick actions, select the three dots and then select ‘Rotate local admin password’:
- Once the device restarts, a new password will be generated.
OR
Endpoint Manager -> Devices -> Windows devices -> select the device à Overview- > On the top bar of quick actions, select the three dots and then select Rotate local admin password.
Powershell:
The ‘Get-LapsDiagnostics’ Powershell cmdlets will collect LAPS logs and tracing from the device. This will create a ZIP file with a lot of helpful troubleshooting data including the config, events logs, & tracing data.
Azure Audit Logs
Windows LAPS events are sent to the Azure audit logs which can be viewed centrally.
Open portal.azure.com > search & navigate to ‘audit logs’. Filter on ‘User agent starts with ‘Windows LAPS’’.
Ranjith

