Overview
Microsoft Office 365 Advanced Threat Protection (ATP) helps protect your organization from sophisticated threats like phishing, malware, and business email compromise. It is crucial to regularly review and optimize ATP settings to ensure your organization’s security remains strong.
The Office 365 ATP Recommended Configuration Analyzer (ORCA) is a PowerShell module designed to evaluate your ATP configuration and provide recommendations based on Microsoft’s security best practices.
In this article, you will learn how to conduct an email security assessment using ORCA, and how to take action based on the insights provided in the ORCA report.
By following the steps outlined here, you’ll be able to review your current email security settings and make necessary improvements to enhance your protection against threats.
Prerequisites
Before using ORCA, make sure the following requirements are met:
- You must have Global Admin or Security Admin permissions in Office 365.
- You need access to PowerShell 5.1 or later.
- Ensure your system is connected to the Internet to install the module from the PowerShell Gallery.
- Your Office 365 tenant should include Microsoft Defender for Office 365 (formerly known as Office 365 ATP).
Steps to Check Office 365 ATP Settings Using ORCA
Step 1: Install the ORCA Module from PowerShell Gallery
- Open PowerShell as Administrator.
- Install the ORCA module by running the following command
Install-Module -Name ORCA- This command downloads and installs the ORCA module from the PowerShell Gallery.
- If prompted to install the NuGet provider or to trust the repository, type
Yand press Enter.
Step 2: Run the ORCA Assessment
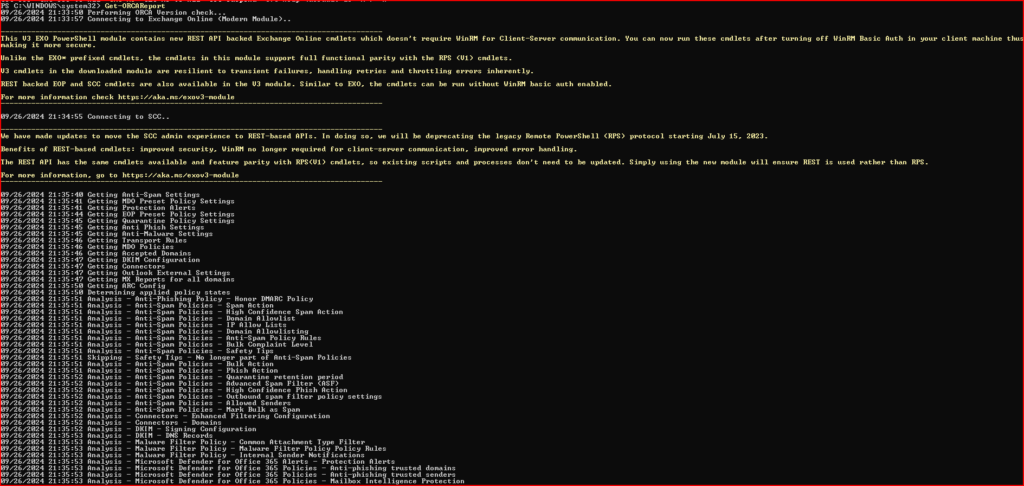
With the ORCA module installed run GET powershell command to connected ORCA, you can now evaluate your ATP settings.
- Run the ORCA script to check your organization’s Office 365 ATP configuration
- Get-ORCAReport
- When it starts, the cmdlet makes some checks, connects to Exchange Online, and then starts to fetch details of the various anti-malware policies configured in the tenant
- ORCA will begin assessing your configuration. It collects data on your existing ATP settings, which may take a few minutes depending on the size and complexity of your tenant.
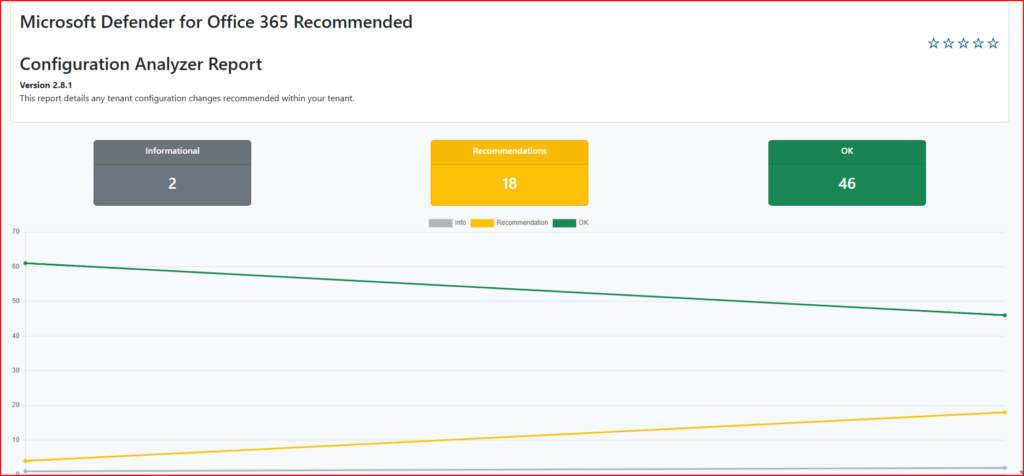
Step 3: Review the ORCA Report
Once the ORCA tool completes its analysis, it generates a detailed report. This report compares your current settings against Microsoft’s security best practices for ATP.
- Report Location: The ORCA report is typically saved in your user profile’s directory, and you will be notified of the exact file path in PowerShell. The report is generated in HTML format for easy review.
- What to Look For:
- Anti-phishing Policies: Check if the policies are configured optimally.
- Safe Links Policies: Review the status and settings of ATP Safe Links.
- Safe Attachments Policies: Ensure ATP Safe Attachments settings follow best practices.
- Spoof Intelligence: Analyze spoof intelligence settings for spoof protection.
- Anti-malware Policies: Confirm that anti-malware policies are configured to detect threats effectively.
- Recommendations: ORCA will provide specific recommendations, such as enabling certain policies, adjusting security settings, and improving coverage for phishing or malware detection.
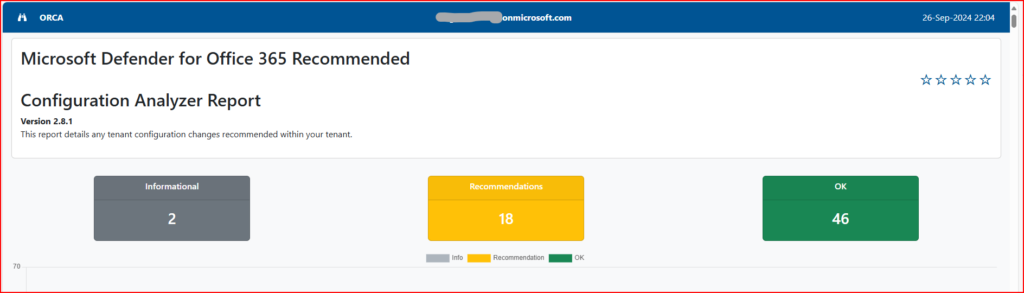
Example of ORCA Recommendations
Here are some common recommendations provided by ORCA:
- Safe Links:
- Recommendation: Enable Safe Links URL protection for all users and ensure that real-time scanning is enabled.
- Action: Implement URL rewriting and real-time scanning in your Safe Links policies to prevent malicious links from harming users.
- Safe Attachments:
- Recommendation: Enable dynamic delivery for attachments.
- Action: Configure ATP Safe Attachments policies to allow email delivery after attachments are scanned for threats.
- Anti-phishing:
- Recommendation: Enable mailbox intelligence to protect against phishing attacks.
- Action: Use mailbox intelligence to detect and mitigate impersonation and other sophisticated phishing attempts.

