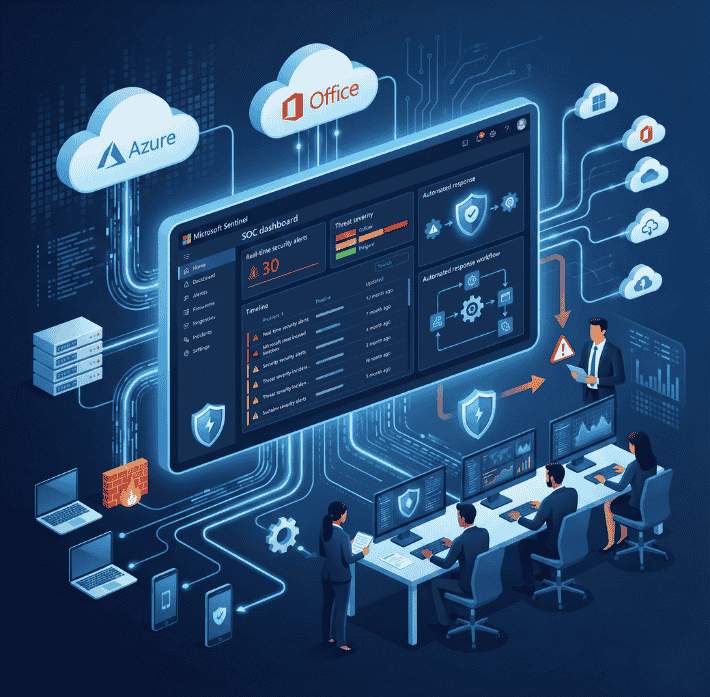
NG Cloud Security’s Microsoft Sentinel services deliver a robust, cloud-native Security Information and Event Management (SIEM) solution designed to strengthen security operations. Microsoft Sentinel enables centralized collection and analysis of security data across users, applications, endpoints, and cloud environments. Our experts implement, configure, and optimize Sentinel to align with your organization’s security requirements. By combining intelligent threat detection, investigation, and automated response, we help security teams identify, understand, and respond to threats faster and more effectively. This approach improves visibility, enhances control over security operations, and supports proactive threat management, helping organizations reduce risk, improve incident response, and maintain a resilient security posture.
Microsoft Sentinel
Microsoft Sentinel

Centralized Security Information and
Event Management (SIEM)
Deployment of Microsoft Sentinel as a cloud-native SIEM solution to collect and analyze security data across your organization. Centralized logging and monitoring of security events from on-premises, cloud, and hybrid environments. Integration with various data sources, including Microsoft 365, Azure, and third-party applications, for comprehensive security visibility.

Threat Intelligence
Integration
Access to Microsoft’s vast threat intelligence feeds, providing up-to-date information on emerging threats. Integration with external threat intelligence sources to enrich security data and enhance detection capabilities. Use of threat intelligence to correlate events and identify potential threats more effectively.

Advanced Threat
Detection and Response
Implementation of machine learning and AI-driven analytics to detect advanced threats in real-time. Customizable detection rules and automated playbooks to respond to incidents quickly and effectively. Continuous monitoring for anomalous behavior, phishing attempts, and other sophisticated attacks.

Customizable Dashboards
and Reporting
Creation of tailored dashboards to provide real-time insights into your security posture. Customizable reporting to meet the needs of different stakeholders, from technical teams to executives. Regular compliance and audit reports to ensure adherence to industry standards and regulations.

Security Orchestration, Automation,
and Response (SOAR)
Automation of repetitive tasks and response actions using Sentinel's built-in SOAR capabilities. Development of automated workflows to handle incident response, threat hunting, and remediation. Integration with existing security tools to streamline operations and improve response times.

Incident Investigation
and Forensics
Comprehensive investigation capabilities to understand the scope and impact of security incidents. Use of built-in tools for deep-dive forensics, including timeline analysis and root cause identification. Collaboration tools for security teams to work together on incident investigations and share insights.

Proactive Threat
Hunting
Use of advanced analytics and hunting queries to proactively search for threats within your environment. Development of custom hunting queries to address specific threats or security concerns. Continuous threat hunting to stay ahead of potential attacks and vulnerabilities.

Security Automation and
Workflow Integration
Integration of Sentinel with Microsoft Power Automate for advanced security automation workflows. Automation of incident triage, threat containment, and remediation processes to reduce response times. Seamless integration with IT service management (ITSM) tools for incident tracking and resolution.

Scalability and
Flexibility
Scalable architecture to handle large volumes of security data, accommodating the needs of growing organizations. Flexibility to adapt Sentinel to various industries and specific security requirements. Pay-as-you-go pricing model to optimize costs while maintaining robust security coverage.
active Clients
projects done
team advisors
Glorious Years
Microsoft Sentinel for Advanced Security Operations
Microsoft Sentinel delivers cloud-native security analytics and automated response to strengthen security operations. NG Cloud Security implements structured SIEM workflows covering data ingestion, correlation, detection, and incident response to reduce risk. Our approach emphasizes use-case mapping, alert tuning, and playbook automation for faster triage. Centralized dashboards provide visibility across identities, endpoints, networks, and workloads. Integrations with Microsoft 365, Azure, AWS, and Google Cloud enable unified monitoring. Continuous optimization, reporting, and compliance alignment improve posture over time. The result is efficient investigations, reduced alert fatigue, and resilient operations that scale securely for modern enterprises with measurable outcomes and governance controls today.

Benefits of Real-Time Threat Detection

Real-Time Threat Detection
Utilize advanced AI and machine learning to detect threats in real-time, reducing the risk of breaches.

Automated Response
Implement automated response actions to quickly contain and remediate threats, minimizing impact.

Automated Response
Implement automated response actions to quickly contain and remediate threats, minimizing impact.


Comprehensive Analysis
Collect and analyze data from across your organization to gain a holistic view of your security environment.

Scalability
Scale your security operations as your organization grows, with a flexible, cloud-native SIEM solution.
Compliance and Audit Readiness
Maintain visibility and reporting for regulations.
What Our Clients Say

CFO & Co-Founder
Greenhive Billing
Alfons F.
Managing Director
Rakesh J.
Vice PresidentHazem Abdel R.
Founder
Oilburg
IT DirectorRead Most
Frequent Questions
Microsoft Entra Suite is a comprehensive identity and access management (IAM) platform that combines advanced tools like SSO, MFA, conditional access, and identity governance to protect users, applications, and data across the organization.
It enforces strong authentication, prevents weak passwords, detects suspicious login behavior, secures privileged accounts, and applies conditional access rules to ensure only verified and compliant users gain access.
SSO allows users to log in once and securely access multiple enterprise applications, improving user experience while reducing password fatigue and related security risks.
Entra Verified ID allows organizations to issue and validate digital credentials securely. This reduces fraud risks, strengthens trust, and simplifies identity verification while giving users control over their personal data.