How Azure Active Directory Services Improve Enterprise Security in 2026
Enterprises face an increasing number of cyber-threats in today’s digital world. These threats target the weakest security link: identity. Securing identity is now a must-have with hybrid work, cloud adoption and more sophisticated attacks. Azure Active Directory Services, now part of Microsoft Entra, provides enterprises with advanced security and governance to protect users and devices. These services will be even more advanced in 2026 to help organizations improve their defenses, lower risks, and adopt a Zero Trust approach.
Identity is the core of security
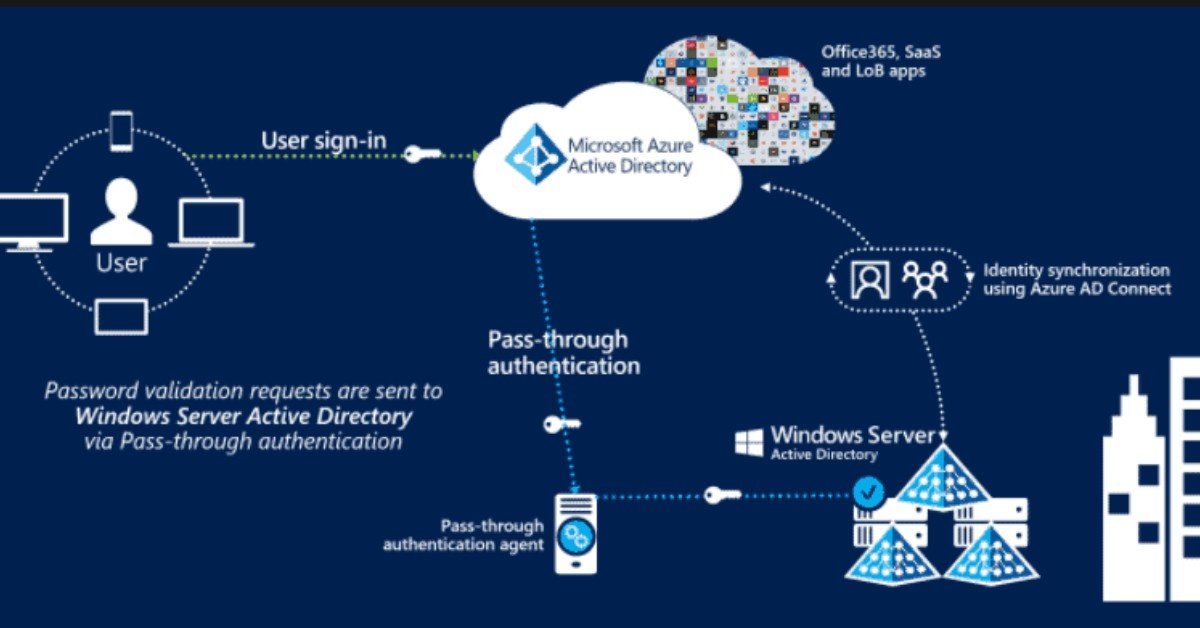
The majority of modern breaches begin with compromised credentials. Attackers exploit vulnerabilities by using phishing, credentials stuffing or incorrectly configured access. Identity has therefore become the new perimeter of security. Azure Active Directory Services are a key component of a hybrid or cloud-native environment, as they provide a cloud-based, unified platform for authenticating users, managing access and enforcing compliance.
2026: Enhanced Conditional access
The expansion of Conditional Access Policies will be one of the most significant improvements in 2026. Now, organizations can apply context-aware, highly granular rules to decide when and how resources are accessible. A user who logs in from a new location might be asked to use multi-factor authentication, while older protocols that are risky may be blocked. Even if an attacker manages to steal credentials, it is much less likely that they will be able to gain entry.
Hybrid Trust and Domain Services
Many enterprises are still using hybrid setups, which combine Active Directory on-premises with cloud identity services. Azure Active Directory Services will support two-way forest relationships in 2026 between on-premises directory services and Entra Domain Services. This allows for smooth interoperability, without exposing enterprise to weak trust models. Support for custom attributes allows businesses to migrate legacy apps securely without compromising security, or creating backdoors which attackers can exploit.
Reduce the risks of legacy protocols
Attackers continue to target legacy authentication methods, such as NTLM or older SSL/TLS protocol. Microsoft is doubling down on restricting or deprecating these weaker authentication methods in 2026. Azure Active Directory Services allows enterprises to enforce modern authentication methods like Kerberos or OAuth. This reduces the risk of relay attacks, credential stealing, and other exploits based on outdated systems.
Better Monitoring and Visibility
A major improvement is the visibility that enterprises have now over identity activities. Azure Active Directory Services provide enhanced auditing, with linkable identifiers. This makes it easier to track suspicious sign-ins and access attempts. Security teams can identify anomalies quickly, investigate risks and implement corrective actions. Conditional Access includes a per-policy report that allows administrators to evaluate the impact of policies before they are rolled out across an enterprise.
Multi-Factor authentication and lifecycle management
Multi-factor authentication has become a necessity for enterprise security. Azure AD’s adaptive MFA will allow users to choose between convenience and security. On the other hand, the identity lifecycle has been improved by automating onboarding and offboarding. It is important to ensure that users who have left the organization do not have access. This eliminates the risk of orphaned or stale accounts.
Role-Based Access and Least Privilege
In enterprise environments, excessive permissions are a silent danger. Azure Active Directory Services addresses this issue with enhanced role-based permissions and tighter boundaries. Administrators can enforce the least privilege principle, giving users only what they need. Combining Privileged Identification Management (PIM), Just-in-Time Access, and Privileged Access Management (JITA), enterprises can reduce the window of opportunities for attackers to try and exploit elevated privileges
Azure AD: Strengthening Zero-Trust with Azure AD
Zero-trust security is not just a goal, it’s a necessity. Azure Active Directory Services, which continuously validates every access request on the basis of identity, device compliance and location, are at its core. Enterprises can now enforce strict controls to verify users and devices each time they attempt to connect. This reduces the attack surface dramatically.
Best Practices for Businesses in 2026
Azure Active Directory Services are a solid foundation. However, to get the most out of them, you must correctly configure and manage it. The following are some best practices:
- Blocking legacy authentication and enforcing strict Conditional Access.
- Implementing multi-factor identification for all users.
- Automating Identity Lifecycle Management to prevent stale accounts.
- Use of Just-in-Time Access and Privileged ID Management for sensitive roles.
- Auditing and monitoring all sign-in activities for anomalies.
- Regularly review RBAC roles to reduce unnecessary permissions.
These practices will help enterprises ensure that their Azure environment is aligned with modern security frameworks.
Conclusion
By 2026, protecting identity will be the most important step that an organization can take to protect itself against cyber threats. Azure Active Directory Services are a powerful set of tools that can be used to reduce risk, enforce security and simplify governance in hybrid and cloud native environments. Integrating these services into Azure Landing Zones will not only improve your enterprise’s security posture, but will also help future-proof it against identity-based attacks that are becoming more sophisticated.
FAQ’s
- What are Azure Active Directory Services and why are they important in 2026?
Azure Active Directory Services provide cloud-based identity and access management. In 2026, they are crucial for enforcing Zero Trust, securing hybrid environments, and protecting enterprises from credential-based attacks. - How does Azure Active Directory Services improve enterprise security in a hybrid setup?
In hybrid environments, Azure Active Directory Services create secure trust relationships between on-premises and cloud directories, enabling seamless authentication while blocking legacy vulnerabilities. - Can Azure Active Directory Services stop cyberattacks caused by stolen credentials?
Yes, by using Conditional Access, adaptive multi-factor authentication, and continuous monitoring, Azure Active Directory Services significantly reduce risks from stolen or compromised credentials. - What new features in 2026 make Azure Active Directory Services more secure?
Key 2025 improvements include advanced Conditional Access, two-way forest trusts, custom attributes support, legacy protocol deprecation, and enhanced auditing with linkable identifiers. - How does Conditional Access enhance identity protection for enterprises?
Conditional Access enforces context-based rules, requiring additional verification when risky login attempts occur, ensuring that attackers cannot misuse compromised credentials effectively.